
ISO Certified Company - Google Rated Number 1
Hacking inplant training
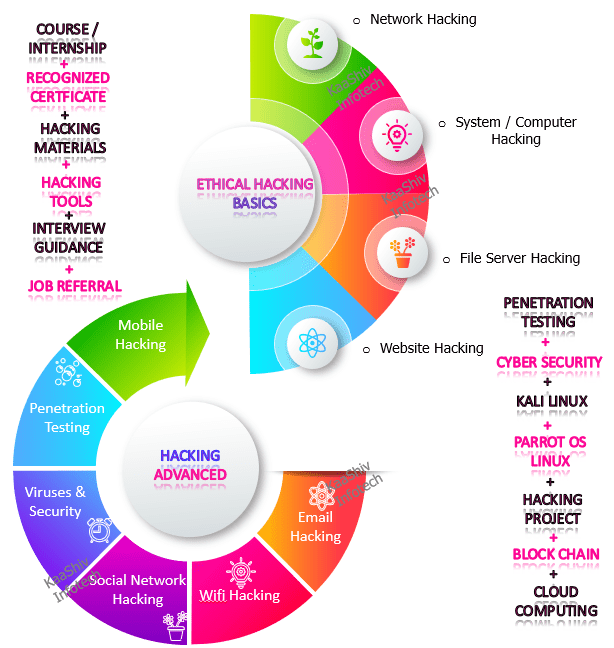
KaaShiv Infotech offers, Hacking inplant training . Inplant Training provides you an in-depth knowledge of Ethical Hacking. This inplant training enables the students to understand and learn the current trend in the job market. Students will prefer trainings to build their profile for their jobs and also for their higher studies. Our company provides both offline and online training for ethical hacking. hacking course in chennai – imparts technical and programming skills on the below list of hacking areas such as,
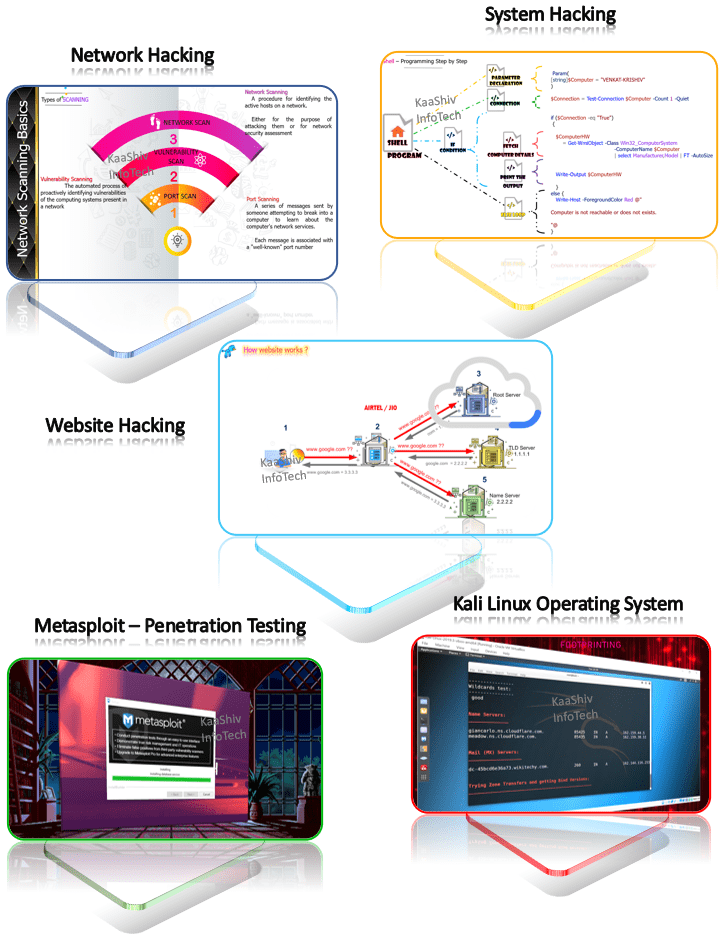
- Network Hacking
- Command Shell Hacking
- System Hacking
- File Server Hacking
- Web Server Hacking
- Website Hacking
- Mobile Hacking
- Penetration Testing
- Social Network Hacking
- Email Hacking
- Wifi Hacking
Highlights of our company
- Common Wealth Bank Recognized Leading Light Rising Star Award Winner
- Run by 10 Years Microsoft Awarded MVP ( Most Valuable Professional )
- Google Recognized Experts and Cisco Recognized Certified Experts
- Microsoft Certified Professionals
- Artificial Intelligence and Robotics Experts
- HCL Technologies Awarded SME ( Subject Matter Expert )
ethical hacking training in chennai
Why our company provides, ethical hacking course in chennai
The Course curriculum for, Inplant training on ethical hacking is carefully researched and prepared by professionals from MNC to meet the demands expected in the current IT industries. After completing inplant training in Chennai at KaaShiv Infotech, students will be familiar with the entire ethical hacking, cyber security, Implementing a hacking project. Below are some insights of our program, hacking course in tamilnadu ,
Trainers to train you
Kaashiv InfoTech Trainers are real-time IT experts and cyber security professionals worked in leading MNCs like
- TCS,
- HCL,
- Infosys,
- Cognizant,
- Wipro

Benefits of Doing an, ethical hacking inplant training
Student can get a real world experience and also our company provides a hands on training in a professional environment. Internships help to getting a chance to try all the possible jobs with explore different options in career.
- As an ethical hacker inplant training , responsibilities would be to –
- Use different strategies to penetrate the security system for finding potential vulnerabilities or errors that can be exploited.
- Recommend better ways to improve the current security posture.
- Co-operate with developers or other security professionals to advise on security needs and requirements.
- Train the staff against different malicious cyber traps.
- Finding the vulnerabilities and improving the security system consumes the major part of an ethical hacker’s life .

Internship for Ethical Hacking and Cybercrime
Inplant Training provides a real time exposure for the students on the latest and trending technologies in the software companies. Below are some Top jobs in IT Industry with very good,
- Network administrator/manager
- Penetration tester
- Web security administrator/manager
- Data security analyst/specialist
- Cyber Security Trainee/Cyber Operations specialist
- Ethical Hacking specialist
- IT Analyst – Vulnerability Management
- Ethical Hacking Application Developer
KaaShiv Infotech Inplant training program horne you in the above-said skills/job roles from basics to advanced.
ethical hacking internship in chennai
Types of Inplant Training to the Students
Learn and Implement
45 Concepts Covering 7 Technologies
+ 1 Projects
Short Term Internship
- Hacking Inplant Training
- Inplant Training on Ethical Hacking – Duration: 1 day, 2 days, 3 days, 5days/ 10days or Based on Student Preference
- Training hours: 3 hrs per day
- Software & other tools installation Guidance
- Hardware support
- Ethical Hacking Inplant training Report creation / Hacking Project Report creation
- KaaShiv Infotech is top under , top 10 ethical hacking institute in tamilnadu , 1 Real time projects – After 6 months of regular Paid Inplant Training , Training becomes free + For best interns Stipend will be provided + Best Interns will be offered Job too.
- Inplant Training Certificate & Industrial exposure certificate + (Achievement certificate for best performers)


S.No |
Ethical Hacking For Inplant Training – Syllabus100% Practical – Live HandsOn – Hacking Inplant Training |
|---|---|
| Topic 1 : | Ethical Hacking Basics
( Introduction Hacking , Job Openings, Mega Breach History , Hacking Terminologies , Elements of Information Security, Motives of Information Security, Information Security Threats Categories , Hacker Classes , Website Info Extraction , Penetration Testing , Bot Website , Website Directory Extraction , SQL injection , Hacking Social Data )
|
| Topic 2 : | Network Hacking
( What is Networking? , Network Scanning Basics , How Network Scanning Works ? , Types of SCANNING , THREE WAY HANDSHAKE , ICMP SCANNING , PING SWEEP SCANNING , TCP Communication FLAGS , Full Open Scan , Stealth Scan – Half-Open Scan , UDP Scan , Check Live System , What is Port Scanning , Lists of Ports , Check Open Ports , Network Mapping , Proxy Servers , Counter Measures )
|
| Topic 3 : | Command Shell Hacking
( What is Operating System , Famous Operating System , Shell Programming, Basic Requirements for Shell , Fetch Computer Hardware, Fetch Computer Total Memory , Fetch Computer RAM Memory, Fetch Hard Disk Details , Command to get system information , Utility to get System Information , Bypass Windows Default execution & increase , Process priority , Installing Packages Using PowerShell , Powerful Copy Command , Fetch RAM Memory Details , Fetch RAM Memory HW Details , Fetch Driver Details , Free Format of Folder Listing , Get list of Tasks Running in Computer , Get list of Services Running in Computer , Delete Files using PowerShell , Delete Folders using PowerShell , Find User Last Login Details , Restart Computer using PowerShell )
|
| Topic 4 : | System Hacking
( How to find IP Address of a Computer , How to find IP Address of a Website Calculate How much data transferred in a network , How to find the path of accessing the website , Find IPV4 and IPV6 details of the Website Server ? , Find Wifi Status , Find Wifi Security Info Find Wifi Password , Get the MAC Address from IP Address , Flush the Network Connection ,Tool to find the Website Owner Details , Tool to Check Website is Alive or not , Tool to Check Computer Information’s heart beat , Tool to Check Processes individually , Check for Windows For errors ,Making Password Never Expires , Find the Security ID of the User , Access Control Panel as a Specific User , Tool to Fetch Complete PC Information , Find the Security ID of the User , Access task Manager information from Tools , Tool to find Users Logged in to the System , Hack Administrator Account , Hack Windows Bypassing using USB , Hack Windows By confusing , Virus Check Software , Memory Hijack Software , USB injection Software Driver Check Software , Browser Clean Software , What is Volume Licensed MS products , Ccleaner – memory cleanup , Malware Threats , Viruses Hacking , Resident Virus , Direct Action , Boot Sector , Multi Partite , Polymorphic , Overwrite , Space Filler Virus , System Hacking Types , Viral Scripting , Hardware Hacking )
|
| Topic 5 : | File Server Hacking
( Anatomy of a FTP Server , How File Transfer Protocol ? , How to move Files to Live Server , Use Specified Authentication to load the Files into Live Server , Check for the port to move data , Using Anonymous Authentication is not secure, Open FTP with Server Name , Anatomy of a FTP IP Address , Open FTP with IP Address , Secure FTP server from Hacking , HTAccess or Any config files , Mobile Memory Access Via FTP Concept )
|
+ Hacking Inplant Training Certificate
+ Free Industrial exposure certificate + (Achievement certificate for best performers) + 1 Hacking Project
Learn and Implement
70 to 400 Concepts Covering 9 Technologies
+ 2 Projects
Long Term Internship
- Hacking Inplant Training
- Inplant Training on Ethical Hacking – Duration: 6 days to 6 Months or Based on Student Preference
- Training hours: 3 hrs per day
- Software & other tools installation Guidance
- Hardware support
- Ethical Hacking Inplant Training Report creation / Hacking Project Report creation
- KaaShiv Infotech is top under, Best hacking Training Institute in Chennai , based 2 real time projects.
- 2 Certificates will be given
- Inplant Training Certificate
- Industrial exposure certificate
- + (Experience Letter for best performers and Researchers)
- Free Hacking Inplant Training / ethical hacking inplant training free – After 6 months of regular Paid Inplant training, Training becomes free + For best interns Stipend will be provided + Best Interns will be offered Job too.


S.No |
ethical hacking course in anna nagar chennai 100% Practical – Live HandsOn – ethical hacking inplant training in chennai |
|---|---|
| Topic 1 : | Ethical Hacking Basics ( Introduction Hacking , Job Openings, Mega Breach History , Hacking Terminologies , Elements of Information Security, Motives of Information Security, Information Security Threats Categories , Hacker Classes , Website Info Extraction , Penetration Testing , Bot Website , Website Directory Extraction , SQL injection , Hacking Social Data ) |
| Topic 2 : |
Network Hacking
|
| Topic 3 : |
Command Shell Hacking
|
| Topic 4 : |
System Hacking
|
| Topic 5 : |
File Server Hacking
|
| Topic 6 : | Web Server Hacking ( What is Root Name Server , How website works ? , How website works ? , How DNS Works , How Dig Tools Works , Server Info Extraction Tool – Part 1 , Server Info Extraction Tool – Part 2 – DNSKEY , Server Info Extraction Tool – Part 2 – DS Record , Anatomy of a Website , How Internet Works , How Website Works , NSLookup Networking Command , Diggint Tool , How to make a Server ? , Server into a Web Server ? , Web Server to World Wide Web Registered Server ) |
| Topic 7 : | Website Hacking ( Information Gathering – FootPrinting , DNS Enumeration , DNS Info Extraction , What is DNS , What is Reverse DNS , Chrome Extension , IP Information of the Website , SPF Record Details , Web Server Information , Website Owner Information , Termux ReconDog , Install Python&GIT , Port Scanning , Who is Lookup , Who is Lookup with software , Who is Lookup with websites , Port Scanning , Honey Pot Server , Reverse IP Lookup , Reverse IP Lookup with websites , Censys – Website Monitor tool , What is Web Session ? , What is Session Hijacking ? , Tor Browsers , Anonymizers , Type of Anonymizers , Anonymizers – Bypass Web Filters , Anonymizers – Bypass Internet Traffic , What is Phishing , Phishing Prevention , What is IP Spoofing , How IP Spoofing works ? , IP Spoofing Basics – How it works ? , IP Spoofing types , IP Spoofing Types – Non-Blind Spoofing , IP Spoofing Types – Blind Spoofing , IP Spoofing Types – Smurf Attack , IP Spoofing Types – MITM Attack , IP Spoofing with Software’s , IP Spoofing with Websites , What is MAC Spoofing , Remote Access VPN , How VPN protocol works ? , VPN Data Encryption , PC VPN Settings , Mobile VPN Settings , IP Spoofing with VPN , How to get Current Ip address ? , Secret mobile Settings for VPN configuration , VPN network configuration with new IP , What is VPN , What is Firewall – Technical Info , IP Spoofing Prevention Technique , Additional Features of Firewall , Firewall Types , Host Based Firewall , How Router works ? , Network Based Firewall , What is Cloaking in Hacking ) |
| Topic 8 : | Mobile Hacking ( Find mobile number details , Access Mobile Number information , Basic Phone Info Package , Install Termux , Access Memory using Termux , Hacking Mobile Task Manager , Networking Cmds in Termux , Ping Command in Termux , Botting Websites , What is an Internet Bot ? , What is a Website Bot ? , What is a BotNet ? , How Hackers attack Website – DOS Attack , How DDOS works , Charter – AntiBot Scanner , Microsoft Safety Scanner , Website Directory Extraction , What is Web Server , Vulnerability testing , Website Vulnerability Analysis ) |
| Topic 9 : | Penetration Testing ( MetaSploit – PenTest Tool , What is MetaSploit , MetaSploit History , MetaSploit Packages , MetaSploit Modules , MetaSploit Sub Modules , How MetaSploit works with Pen Testing , How Exploits works in Metasploit ? , Metasploit Architecture , Metasploit Library , Metasploit Codes , Metasploit Tools , Metasploit Command Basics , Modules in Metasploit , Create and Setup Exploit, Attack Target , Fetch the injected Virus Path , Make Directory to Control Target , Injecting Files in to the Target Machine , Idle time and IP Details of the Target , Keyboard Hacking/Password Attacks , Audio Recording , Hacking Screenshot of Target , Hacking Screen of the Target , Hack Camera Details in the Target , Hack Camera Take snap of the Target , Hack Camera Take Live Video of the Target , How to install Metasploit in Mobile , How to search Metasploit packages , Find open ports using Metasploit in target ) |
| Topic 10 : | Social Network Hacking ( find fb id , Find facebook friends using termux – Facebook Tricks ) |
| Topic 11 : | Email Hacking ( Email Spoofing , Mail Tracking with gmail , Send mail to find location ) |
| Topic 12 : | Wifi Hacking ( Wifi Introduction – Basic components of Wifi , How Wifi works , Wireless Devices, Get Basic Wifi Accounts Stored in the Computer , Get Wifi interfaces Stored in the Computer , Get Wifi Properties Stored in the Computer , How to Export Wifi Passwords , How to get Windows Wifi Password ) |
| Topic 13 : | Kali Linux – Hacking Operating System ( Introduction , FootPrinting Tools, Backdoor Attack Tools , Reconnaisance Tools , Sniffing Tools ) |
| Topic 14 : | Parrot OS – Hacking Operating System ( Anonymous Access – Be a Hacker , No one can hack you , Control your network usage , Control your computer Execution , Control anyone in the Network ) |
+ Hacking Inplant Training Certificate
+ Free Industrial exposure certificate + (Achievement certificate for best performers) + 2 Hacking Projects
Ethical Hacking Course Training in Chennai
Apply for inplant training - Contact Us
Contact Number / Whatsapp Number
Mobile 2 : 7667664842
Mobile 3 : 9840678906
Ethical Hacking Online Internship
Sample Video – Ethical Hacking Course
Hacking training and internship – Demo Link :
Check out our Sample Content under the topics ” hacking inplant training in chennai “
Check our Previous testimonials from students from Different Countries and Different States :
Check our students, Internship feedback kaashiv infotech reviews
More about our Company
Hacking inplant training
Our, Learn Ethical Hacking Online - Training Youtube Channels –
Our Technology Channel :
https://www.youtube.com/channel/UC2MYZHG8a56u4REI2RedtRA
Our Subject Channel :
https://www.youtube.com/channel/UC9dcBYLL-ZGTy7ml8YMTlag/videos
Check out the colleges attended our Internship :
Click to view more details kaashiv infotech inplant training reviews
Intern Students Feedback
Check our ( Intern )Students Feedback :
Inplant training in chennai for hacking – Feedback – https://www.kaashivinfotech.com/inplant-training-feedback
Hacking Internships – Feedback – interns for hacking students
Our Live Project:
We ranked Top 2000 technological companies in India, www.wikitechy.com

YEARS OF EXPERIENCE COMPANY

PROFESSIONAL EXPERTS
/ TRAINERS

SUCCESSFUL COMPLETED STUDENTS

COLLEGE
STUDENTS
PARTICIPATED
1. Report for the inplant training will be provided after the completion of the programme.
2. Regular tech updates to the students.
3. Free inplant training Projects given
1. Industry Recognized, certificate for inplant training will be given.
2. Certificates will be given ( Inplant Training Certificate & Industrial exposure certificate ) + (Achievement certificate for best performers)
2 day / 3/ 4 / 5 / 10, 20 days or 1 month to 6 Months ( Any Number of Days – Based on student preferences)
Specialized technologies from, Hacking inplant Training
online internship for ethical hacking
ethical hacking internship work from home
hacking inplant training for freshers / hacking inplant training for students
- This inplant training can be done by the freshers to build their career. This program will provide a clear baseline for entry-level engineers to enter the IT industry.
- Before entering into the companies, doing the training will give you more clarity in the programming field.
- Kaashiv Infotech recommends that all department students, freshers, and even school students take up this training and build their careers.
Summer Training On Ethical Hacking
- hacking summer training – This program becomes mandatory before completing their degree for computer science-based students Due to its huge involvement and implementation flexibility in many fields.
- hacking training summer – The reason for doing a hacking inplant training is, real-time industrial exposure is preferred by most of the companies in India. Identifying real-time training with a recognized inplant certificate is very important.
- After completing the training will acquire practical knowledge, analytical skills, programming skills and problem-solving skills.
Hacking winter inplant training
- Inplant training can be done by diploma studying students, engineering students or freshers and art college students too.
- We are inviting highly excited students, who are interested in winter research & development program. The selected students will have the chance to work with Kaashiv Research & Development team.
- In this hacking inplant training, the students will also have the chance to join in the workshops, events, live projects of the main industrial research organization in the world and network with other students in different fields from another field.
- This Ethical Hacking Winter Inplant Training makes your career in IT Security. We have advance Ethical Hacking modules for this winter training in Ethical Hacking.
hacking inplant training online
- Learn Ethical Hacking Online – kaashiv infotech company offers online training for the students or professionals who prefer, hacking inplant training work from home .
- Hacking intern will be learning cutting-edge technology based on hacking online classes. Our, online hacking training program provides Online portal to study anytime, online classes to study flexibly, industry-recognized certificate, hacking interview questions for all the attendees.
- ethical hacking jobs in india – Most of the students will be getting ready for campus placement or off campus interviews.
- Applying basic theoretical ideas into the real world via internship programs horne their skills to the next level of industry knowledge.
- Outcome of this , hacking Inplant Training is :
- Student will be specialized in cyber security and ethical hacking programming.
- Students will be getting trained in / writing 10 Programs – Will change based on the duration of the program.
- 1 Project and project report will be given at the end of the program.
More Question on, Hacking Inplant Training
Is ethical hacking a good career ?
The answer to this question is Yes. Ethical hacking is a good career option when you have an interest and passion for it. There is a lot of opportunity for ethical hacking all over the world with good packages.When we talk about hacking, here there is both ethical and Unethical hacking we say it in other terms like a white hat and black hat hacking. Generally, people learn to hack according to their interests whether they want to use it for good purposes or for bad purposes.
Which startups provide the best inplant training in hacking in India ? What are the duration of these trainings ? Also, are these inplant trainings free or stipend based ?
- The Answer is, Kaashiv Infotech offers inplant training .This training involves, practical knowledge and real-time experience. Inplant training duration can be from 1 day to any number of days, like 6 months. Usually, students will prefer 5 days to 6 months of trainings
What are the companies in India that will offer me a job by considering my ethical hacking knowledge, and what salary can I expect ?
- ceh jobs for freshers – I guess the companies would be improved judges of your knowledge.
- Your salary can vary from high to low depending on level of your knowledge in ethical hacking.
- To find out what, ethical hacking companies in india – are offering jobs , use LinkedIn or any other job seeking portals.
How can I get inplant training on Ethical hacking ?
- The Answer is, Kaashiv Infotech provides inplant training on Ethical hacking & cyber security. You can apply for inplant training via the link and get confirmation from the team and attend our training on the specified requested date.
Which is the best institute for - Online Cyber Security & Ethical Hacking Inplant Training ?
- The Answer is, Kaashiv Infotech company is the best institute for online cyber security and ethical hacking training.
- For an online training you can refer to this link ethical hacking internship (or) you can contact our customer care 7667662428 . our team will help you.
Who is eligible for ethical hacking ?
ethical hacking course eligibility – Students belonging to 1st year, 2nd year, 3rd year and 4th year Computer science Engineering or Information Technology Engineering & Electronics, Instrumentation, Electronics and Telecommunications and Biomedical engineering can apply for this hacking training
What is the duration of hacking inplant training ?
- hacking course in chennai fees details – hacking training fees and duration – is 10 / 20 / 30 / 40 / 50 hours or Any Number of Days ( based on your student preference ) and if you want to know about this course fees, you can visit our kaashiv infotech company directly
Is there any good company in India to do inplant training in ethical hacking ?
Kaashiv infotech is the best company to do trainings in ethical hacking. Hacking is the much-exploited stadium of information technology & security. It has now become a billion-dollar industry.
Hacking was termed as a programming subgroup of the developers’ community. But later it was disguised by the moron media people who little understand hacking, and the technology behind the security.
How to get training in ethical hacking ?
- The answer is – Kaashiv infotech provides, training in ethical hacking . This training involves learning and developing applications. Various technology trainings are,
Hacking Interview Questions and Answers
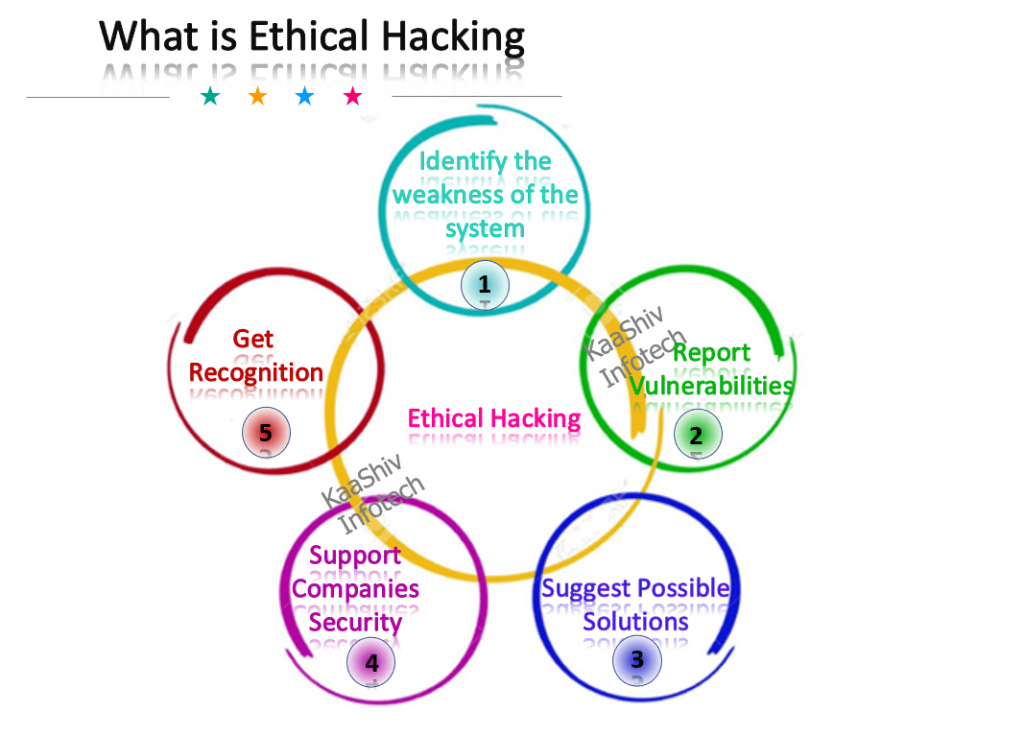
What is ethical hacking ?
- Ethical Hacking is when the individual is allowed to hacks the systems with the authorization to the stock owner to search out of weakness in an exceedingly system and the later fix them.
What are the types of ethical hackers ?
- Grey Box hackers
- Black Box penetration Testers
- White Box penetration Testers
What is IP address and Mac address ?
- IP address : To every device to an IP address is allocated, so that device can be located to the network.
- MAC (Machine Access Control) address : A MAC address is the unique serial number allocated to the each network interface on each device.
What is the DOS (Denial of service) attack ?
- Denial of Service, is a malicious attack on network that is complete by overflowing the network with unusable to traffic. Though, DOS does not cause any theft of the data or security breach, it can cost the website owner is great deal of money and time.
What are the common forms of the DOS attack ?
- Buffer Overflow Attacks
- Smurf Attacks
- Viruses
- SYN Attacks
- Teardrop Attacks
What is SQL injection ?
- SQL injection techniques used to steal data from the organizations, it is a fault to create in the application code. SQL injection happens to when you inject the content into an SQL query string and the output mode of content into a SQL query string, and the result modifies the syntax of your query in the ways you did not mean.
What are the types of computer based on social engineering attacks ?
Computer based social engineering attacks is,
- Phishing
- Baiting
- Online scams
List out common tools used by Ethical hackers ?
- MetaSploit
- WireShark
- NMAP
- Maltego
What is Phishing ?
- Phishing method includes sending of false emails, chats or website to the copy real system with aim of stealing data from the original website.
What are the advantages and disadvantages of hacking ?
Advantages
- It can be used to stop security attacks
- To plug the bugs and loopholes
- It helps to prevent data theft
- Hacking prevents malicious attacks
Disadvantages
- It makes massive security issues
- Get illegal system access
- Stealing private information
- Violating privacy regulations
What is the Burp Suite ?
- It is an integrated platform used for the attacking web applications. It contains of all the Burp tools a mandatory for attacking an application. Burp Suite tool has to same approach for the attacking web applications like framework for handling HTTP requests, upstream proxies, alerting, logging and so on.
Difference between hacking Vs. Ethical Hacking ?
- Hacking: It defines the banned way of accessing the system (Unauthorized Access)
- Ethical hacking: Official way of accessing the system (Penetration testing)
Why ethical hacking ?
- To find errors and vulnerabilities
- To determine the risk to the organization
What are the types of penetration testing ?
- Black box: No previous knowledge of network
- White box: Knowledge of remote network
Name top 10 vulnerability
- Injection
- Broken Authentication
- Sensitive data exposure
- XML External Entities (XXE)
- Broken Access control
- Security misconfigurations
- Cross Site Scripting (XSS)
- Insecure Deserialization
- Using Components with known vulnerabilities
- Insufficient logging and monitoring
What is CSRF (Cross Site Request Forgery)? How you can prevent this ?
- CSRF is an attack from a malicious website that will send a request to a web application that a user is previously authenticated against from a different website. To prevent CSRF you can add random challenge token to each request and associate them with user’s session. It makes sure the developer that the request received is from a valid source.
What is the Network Sniffing ?
- Network Sniffing method is used to monitors data flowing over the computer network links. By allowing you to capture and view the packet to level data on your network, sniffer tool can help you to the find network problems. Sniffers can be used for both stealing data off the network and also for genuine network management.

