
ISO Certified Company - Google Rated Number 1
Hacking Course
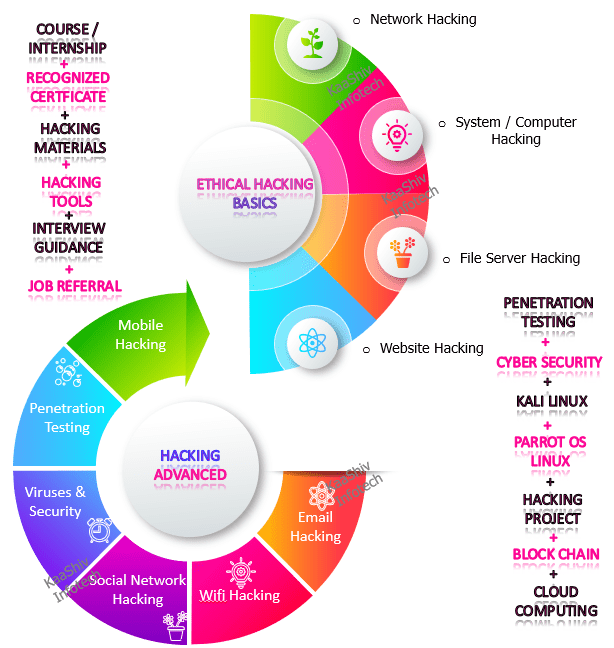
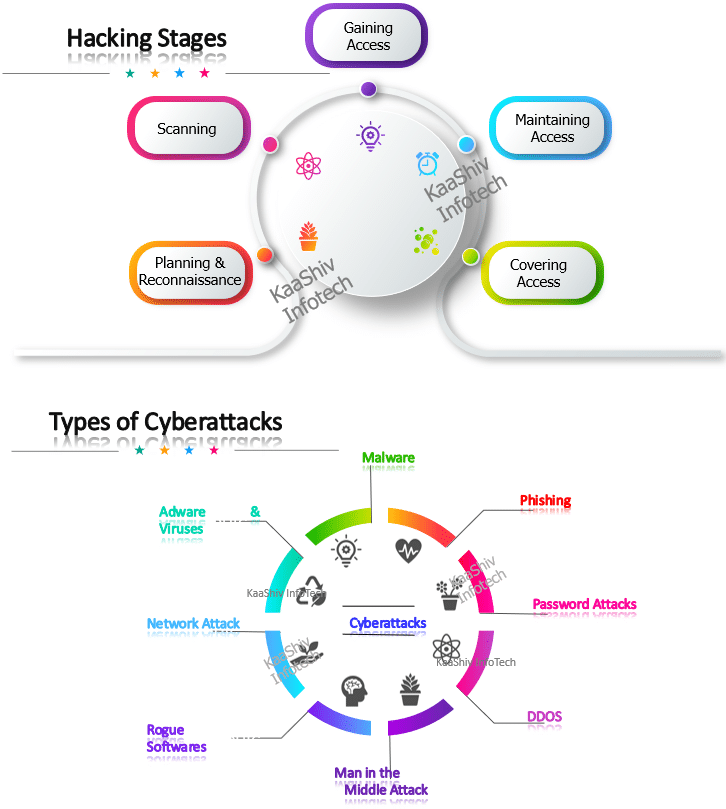
KaaShiv Infotech offers, hacking course . Our, hacking course in india – provides you an in-depth knowledge of Ethical Hacking. This training enables the students to understand and learn the current trend in the job market. Students will prefer ” ethical hacking training ” to build their profile for their jobs and also for their higher studies. Our company provides both offline and online ethical hacking. Ethical Hacking Course in Chennai – imparts technical and programming skills on the below list of hacking areas such as,
- Network Hacking
- Command Shell Hacking
- System Hacking
- File Server Hacking
- Web Server Hacking
- Website Hacking
- Mobile Hacking
- Penetration Testing
- Social Network Hacking
Highlights of our company
- Common Wealth Bank Recognized Leading Light Rising Star Award Winner
- Run by 10 Years Microsoft Awarded MVP ( Most Valuable Professional )
- Google Recognized Experts and Cisco Recognized Certified Experts
- Microsoft Certified Professionals
- Artificial Intelligence and Robotics Experts
- HCL Technologies Awarded SME ( Subject Matter Expert )
hacking internship
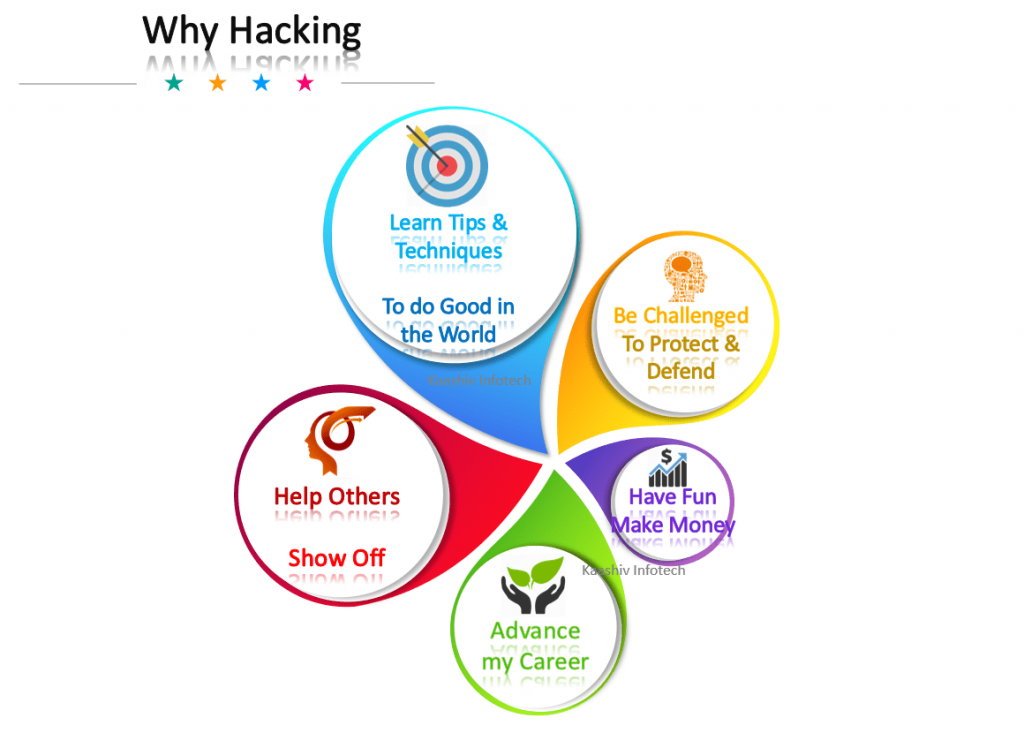
Why our company provides, Ethical Hacking Courses and Training
Ethical hacking course – is carefully researched and prepared by professionals from MNC to meet the demands expected in the current IT industries. After completing the hacking course at KaaShiv Infotech, students will be familiar with the entire ethical hacking, cybersecurity. Below are some of the insights of our programme, hacking course in tamilnadu ,
Trainers to train you
Our, hacking course chennai – Program Trainers are real-time IT experts and cyber security professionals worked in leading MNCs like
- TCS,
- HCL,
- Infosys,
- Cognizant,
- Wipro

Benefits of Doing an, ethical hacking training
- With the improved cyberthreats and cybercrime a main of the professional organizations are in the dire need of Ethical Hackers to defend the hacking threats that could occur in their security systems.
- Vulnerabilities in the Security systems lead a company’s whole network system vulnerable to malware and threats. Further with the ever-growing use of technology, threats like ransomware, viruses, DDoS attacks, Network hacking, website hacking are increasing significantly and this authorized the need for Ethical Hackers who can combat the threats and protect the whole company’s digital security.
- Also, Ethical Hackers are not only needed in the IT industry but across a range of businesses like Banking, Airlines, Telecom Companies, Cyber-crime, Government Agencies, E-commerce stores, Internet providers.
- Hacking course in Chennai at Kaashiv Infotech provides the required training and improves the skills that are required for a professional Ethical Hacker under the guidance of our expert mentors.
.

Ethical hacking course and jobs
Ethical Hacking Training provides a real time exposure for the students on the latest and trending technologies in the software companies. Below are some of the, ethical hacking certification jobs :
- Network administrator/manager
- Penetration tester
- Web security administrator/manager
- Data security analyst/specialist
- Cyber Security Trainee/Cyber Operations specialist
- Ethical Hacking specialist
- IT Analyst – Vulnerability Management
- Ethical Hacking Application Developer
KaaShiv Infotech Training programme horne you in the above said skills / job roles from basics to Advanced.
Free Ethical Hacking Tutorials for Beginner
Hacking Course Training to the Students
Learn and Implement
70 to 400 Concepts Covering 9 Technologies
+ 3 to 4 Projects
Hacking Course Structure
- Hacking Course Duration : Week Day / Week End – Any Day Any Time – Students can come and study
- Training hours: 50 hrs
- Software & other tools installation Guidance
- Hardware support
- Hacking Course Materials / Hacking Project Report creation
- KaaShiv Infotech is top under, hacking course in chennai , based 3-4 real time projects.
- Certificates will be given
- Course Completion Certificate
- Industrial exposure certificate
- + (Achievement certificate for best performers and Researchers)


S.No |
ethical hacking course near me 100% Practical – Live HandsOn – hacking course free
|
|---|---|
| Topic 1 : | Ethical Hacking Basics ( Introduction Hacking , Job Openings, Mega Breach History , Hacking Terminologies , Elements of Information Security, Motives of Information Security, Information Security Threats Categories , Hacker Classes , Website Info Extraction , Penetration Testing , Bot Website , Website Directory Extraction , SQL injection , Hacking Social Data ) |
| Topic 2 : |
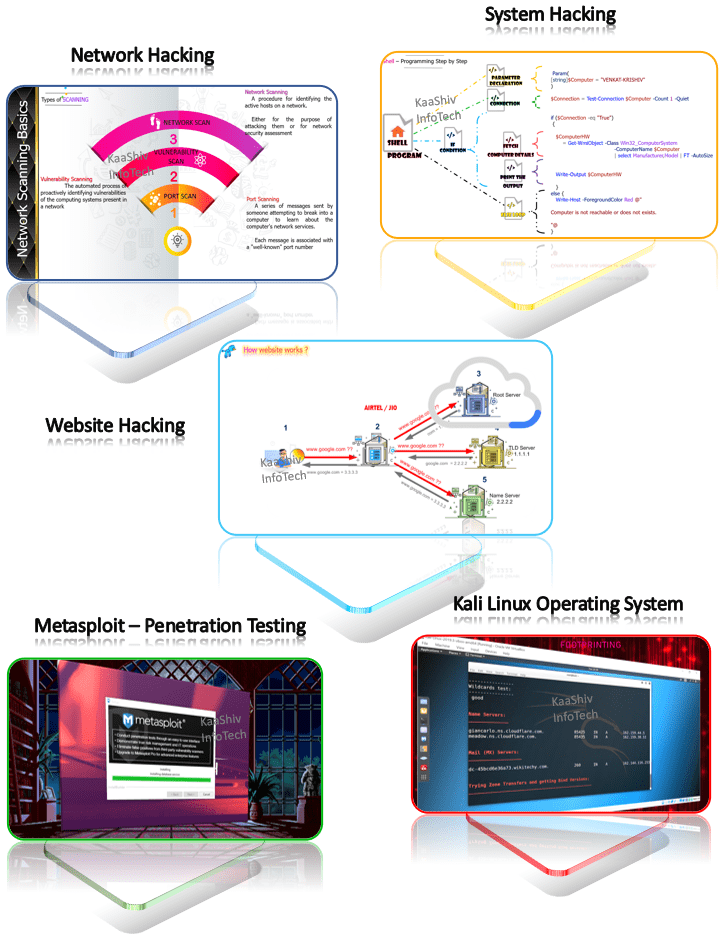
Network Hacking
|
| Topic 3 : |
Command Shell Hacking
|
| Topic 4 : |
System Hacking
|
| Topic 5 : |
File Server Hacking
|
| Topic 6 : | Web Server Hacking ( What is Root Name Server , How website works ? , How website works ? , How DNS Works , How Dig Tools Works , Server Info Extraction Tool – Part 1 , Server Info Extraction Tool – Part 2 – DNSKEY , Server Info Extraction Tool – Part 2 – DS Record , Anatomy of a Website , How Internet Works , How Website Works , NSLookup Networking Command , Diggint Tool , How to make a Server ? , Server into a Web Server ? , Web Server to World Wide Web Registered Server ) |
| Topic 7 : | Website Hacking ( Information Gathering – FootPrinting , DNS Enumeration , DNS Info Extraction , What is DNS , What is Reverse DNS , Chrome Extension , IP Information of the Website , SPF Record Details , Web Server Information , Website Owner Information , Termux ReconDog , Install Python&GIT , Port Scanning , Who is Lookup , Who is Lookup with software , Who is Lookup with websites , Port Scanning , Honey Pot Server , Reverse IP Lookup , Reverse IP Lookup with websites , Censys – Website Monitor tool , What is Web Session ? , What is Session Hijacking ? , Tor Browsers , Anonymizers , Type of Anonymizers , Anonymizers – Bypass Web Filters , Anonymizers – Bypass Internet Traffic , What is Phishing , Phishing Prevention , What is IP Spoofing , How IP Spoofing works ? , IP Spoofing Basics – How it works ? , IP Spoofing types , IP Spoofing Types – Non-Blind Spoofing , IP Spoofing Types – Blind Spoofing , IP Spoofing Types – Smurf Attack , IP Spoofing Types – MITM Attack , IP Spoofing with Software’s , IP Spoofing with Websites , What is MAC Spoofing , Remote Access VPN , How VPN protocol works ? , VPN Data Encryption , PC VPN Settings , Mobile VPN Settings , IP Spoofing with VPN , How to get Current Ip address ? , Secret mobile Settings for VPN configuration , VPN network configuration with new IP , What is VPN , What is Firewall – Technical Info , IP Spoofing Prevention Technique , Additional Features of Firewall , Firewall Types , Host Based Firewall , How Router works ? , Network Based Firewall , What is Cloaking in Hacking ) |
| Topic 8 : | Mobile Hacking ( Find mobile number details , Access Mobile Number information , Basic Phone Info Package , Install Termux , Access Memory using Termux , Hacking Mobile Task Manager , Networking Cmds in Termux , Ping Command in Termux , Botting Websites , What is an Internet Bot ? , What is a Website Bot ? , What is a BotNet ? , How Hackers attack Website – DOS Attack , How DDOS works , Charter – AntiBot Scanner , Microsoft Safety Scanner , Website Directory Extraction , What is Web Server , Vulnerability testing , Website Vulnerability Analysis ) |
| Topic 9 : | Penetration Testing ( MetaSploit – PenTest Tool , What is MetaSploit , MetaSploit History , MetaSploit Packages , MetaSploit Modules , MetaSploit Sub Modules , How MetaSploit works with Pen Testing , How Exploits works in Metasploit ? , Metasploit Architecture , Metasploit Library , Metasploit Codes , Metasploit Tools , Metasploit Command Basics , Modules in Metasploit , Create and Setup Exploit, Attack Target , Fetch the injected Virus Path , Make Directory to Control Target , Injecting Files in to the Target Machine , Idle time and IP Details of the Target , Keyboard Hacking/Password Attacks , Audio Recording , Hacking Screenshot of Target , Hacking Screen of the Target , Hack Camera Details in the Target , Hack Camera Take snap of the Target , Hack Camera Take Live Video of the Target , How to install Metasploit in Mobile , How to search Metasploit packages , Find open ports using Metasploit in target ) |
| Topic 10 : | Social Network Hacking ( find fb id , Find facebook friends using termux – Facebook Tricks ) |
| Topic 11 : | Email Hacking ( Email Spoofing , Mail Tracking with gmail , Send mail to find location ) |
| Topic 12 : | Wifi Hacking ( Wifi Introduction – Basic components of Wifi , How Wifi works , Wireless Devices, Get Basic Wifi Accounts Stored in the Computer , Get Wifi interfaces Stored in the Computer , Get Wifi Properties Stored in the Computer , How to Export Wifi Passwords , How to get Windows Wifi Password ) |
| Topic 13 : | Kali Linux – Hacking Operating System ( Introduction , FootPrinting Tools, Backdoor Attack Tools , Reconnaisance Tools , Sniffing Tools ) |
| Topic 14 : | Parrot OS – Hacking Operating System ( Anonymous Access – Be a Hacker , No one can hack you , Control your network usage , Control your computer Execution , Control anyone in the Network ) |
+ Course Completion Certificate
+ Free Industrial exposure certificate + (Achievement certificate for best performers) + 3 Hacking Projects
Hacking Inplant Training
Apply for Course - Contact Us
Contact Number / Whatsapp Number
Mobile 2 : 7667664842
Mobile 3 : 9840678906
Hacking course for beginners free
Sample Video – Ethical hacking courses to learn
Ethical Hacking training and Course – Demo Link :
Check out our Sample Content under the topics ” ethical hacking training online ” hacking student course
Check our Previous testimonials from students from Different Countries and Different States :
Check our students, Course feedback kaashiv infotech reviews
More about our Company
Ethical Hacking Training in Chennai
Our, Ethical hacking training videos
Our Technology Channel :
https://www.youtube.com/channel/UC2MYZHG8a56u4REI2RedtRA
Our Subject Channel :
https://www.youtube.com/channel/UC9dcBYLL-ZGTy7ml8YMTlag/videos
Check out the colleges attended our Course :
Click to view more details ethical hacking training in chennai
Intern Students Feedback
Check our ( Intern )Students Feedback :
Inplant training in chennai for hacking – Feedback – https://www.kaashivinfotech.com/inplant-training-feedback
Hacking Course – Feedback – interns for hacking students
Our Live Project:
We ranked Top 2000 technological companies in India, www.wikitechy.com

YEARS OF EXPERIENCE COMPANY

PROFESSIONAL EXPERTS
/ TRAINERS

SUCCESSFUL COMPLETED STUDENTS

COLLEGE
STUDENTS
PARTICIPATED
1. Ethical hacking training report will be provided after the completion of the programme.
2. Regular tech updates to the students.
3. Free Course Projects given
1. Industry Recognized, Course Certificate will be given.
2. Certificates will be given ( Course Completion Certificate & Industrial exposure certificate ) + (Achievement certificate for best performers)
2 day / 3/ 4 / 5 / 10, 20 days or 1 month to 6 Months ( Any Number of Days – Based on student preferences)
Specialized technologies from, hacking course in tamilnadu
Cyber Security training in Chennai
Ethical hacking courses free
Hacking Course for beginners
- This hacking course also targeted at whole beginners and is an extraordinary offering when it comes to securing the subject matter like a pro.
- Hackers invented this course and is now famous among many ethical hacking candidates.
- It treats its students as children and developments you throughout the minefield of ethical hacking one step at a time.
Hacking summer training
- This programme becomes mandatory before completing their degree for computer science based students Due to its huge involvement and implementation flexibility in many fields.
- The reason for doing, ethical hacking course after 12th – you will be getting real time industrial exposure is preferred by most of the companies in India. Identifying real time course with recognized Course certificate is very important. After completing the ethical hacking course will acquire practical knowledge, analytical skills, programming skills and problem-solving skills.
Hacking Winter training
- Hacking training can be done by diploma studying students , engineering students or freshers and arts college students too.
- Students can prefer the trainings in the winter holidays too. Doing a meaningful learning in the holidays is the best and first step towards the vision of success. The reason is, your career is getting enhanced and Practical knowledge with programming skills carves the hacking students towards cutting edge technologies.
Hacking Course online
- Hacking course Online – kaashiv Infotech offers, hacking course online – for the students or professionals who prefer, hacking course work from home .
- hacking course free online (or) hacking course online free – Hacking students will be learning cutting edge technology based on hacking online classes . Our, hacking best courses – programme provides Online portal to study anytime, online classes to study flexibly , industry-recognized certificate with, hacking interview questions – for all the attendees.
- Ethical Hacker will teach you the modern commercial-grade hacking tools, methods, and procedures used by hackers and information security professionals to legally hack an organization.
- ethical hacking certification salary – Different skills can affect your salary. Below are the most popular skills and their effect on salary.
- Network Management / Administration
- IT Security & Infrastructure
- Computer Security
- ethical hacking certification path – Explore the common career paths for Ethical Hacker. Teams with Ethical Hacker in their job title in Delhi, Delhi earns an average of 19.5% more than the national average. These job titles also find higher than normal salaries in Chennai .
- ethical hacking course eligibility – While selecting a path professionally one needs to have some of the basic eligibility for the course. Passed 10+2 in any related stream
More Question on, Ethical hacking Course
What stream should I take after 10th to become an ethical hacker ?
- ethical hacking course after 10th – To become an ethical hacker, I would recommend that you take up Physics, Chemistry and Maths along with computers (Java/Python/C++) whichever your school may provide you with.
- The knowledge of one of these programming languages would give you an advantage as when people your age would be studying the language then at that time you could study the concepts of hacking and things related to Linux based Operating system and networking.
How much time required to learn ethical hacking ?
- Hacking is an in-depth field that takes years to master. It all depends on the total time you put into learning to hack per day. But you should have a basic knowledge of programming language before you can pursue hacking. A people can get a moderate skillset in two years if they are fully dedicated to this task.
- Depending on the Ethical hacking course you are taking, the Ethical Hacking certification program takes five days to complete.
What is the eligibility to join in ethical hacking course ?
- Eligibility for ethical hacking course – It doesn’t require any eligibility you can join course in Kaashiv Infotech Company. But you need technical knowledge so that it will be easy to know some terminology.
- But for government and college institutions you need 10+2 and IT experience of 2 years in school or college. Ethical hackers want only on certificate to join any company and hacking experience and knowledge
How can I become an ethical hacker after class 12 ?
- ethical hacking courses after 12th – Hacking is just for those who have interest in programming, who are creative and who have computers. It does not require any, ethical hacking course age limit or qualifications.
- First of all, you must develop your interest in programming. Instead of windows try to learn Linux and start work on it. If you want to become ethical Hacker then you can join many institutes like Kaashiv Infotech company and pursue cyber security course in it.
- Learn various programming languages first like c, c++, c#, python etc……
what are the benefits of ethical hacking ?
Benefits of ethical hacking training
- It prepares students to handle information security with more simplicity .
- Knowledge in cutting-edge Hacking concepts – hacking Mobile devices & smart phones, writing Virus codes.
- Better knowledge of IDS, Firewalls and Wireless Hacking .
- Handling of latest development in mobile and web technologies including Android OS 4.1 and Apps, iOS 6 and Apps, BlackBerry 7 OS, Windows Phone 8 and HTML 5 .
- Advanced Log Management for Information Assurance .
Can i do ethical hacking after 12th ? (or) can i study ethical hacking after 12th ?
- After 10th class, you should choose for PCM(Physics, Chemistry and Mathematics) stream with Computer Science. After 12th, you can choose for B. Tech, BSC in Computer Science, BE or IT engineering. There are many organizations like kaashiv infotech offer specialised courses related to hacking also.
What are the advantages of ethical hacking ?
- To have a computer system that stops malicious hackers from gaining access.
- To recover the missing information, particularly in case you lost your password.
- To perform penetration testing to strengthen computer and network security.
- To put adequate preventative measures in place to stop security breaches.
Is ethical hacking a good career ?
How to become an ethical hacker after 12th ?
- If you are in 12th and if you have finished 12th, you must have some skills prebuilt in you
- Networking basics.
- Html basics.
- Some basic knowledge to use linux and computer.
- And if you don’t have those all, you should not start your journey as an ethical hacker. By not getting started I mean to say: start but, you need to work so hard to learn new things.
- Because, as you will be starting your btech or something like that, it will be hard for you to learn these given 3 things and do your subjective activities. so, my information will be that, if you have time, start learning html,networking,basics of computer, then enter into vulnerability testing etc.
which course is best for ethical hacking (or) which ethical hacking course is best ?
How many years course is ethical hacking ?
Following are the highlights of – ethical hacking course with certificate
- Course Name – Cyber Security & Ethical Hacking
- Course Type – Certificate Course
- Course Duration – Varies (3 months to 2 years)
- ethical hacking course qualification – Students from 1st Year Student / 2nd Year Student / 3rd Year Student / 4th Year Student / Passed Out Student / Freshers and Professionals interested to learn.
- Career Options – Ethical Hacker, Information Security Analyst, Penetration Tester, Information Security Manager, Security Consultant
- ethical hacking certification for beginners / ethical hacking certification free / ethical hacking certification test – Industry recognized certificates will be provided for the students who perform training in our company based on Ethical Hacking.
Which is the best ethical hacking training center in India & What Courses are needed for ethical hacking?
Kaashiv infotech company is the best – ethical hacking training center in india .
ethical hacking courses list :
- Network Hacking
- Command Shell Hacking
- System Hacking
- File Server Hacking
- Web Server Hacking
- Website Hacking
- Mobile Hacking
- Penetration Testing
- Social Network Hacking
- Email Hacking
- Wifi Hacking
why to learn ethical hacking ?
- It is the hacker who builds the computer system in such a way that would protect the access of the hacker and would ensure that the protection system is well used.
- It is the hacker who makes the malicious attack from unknown source gets protected.
- Such a person is capable to use protective measures to avoid any kind of security openings
- To make sure the user information is well protected, the hacker comes up with a new solution.
- It is the hacker who safeguards that the network is tested on the regular note.
Hacking Interview Questions and Answers
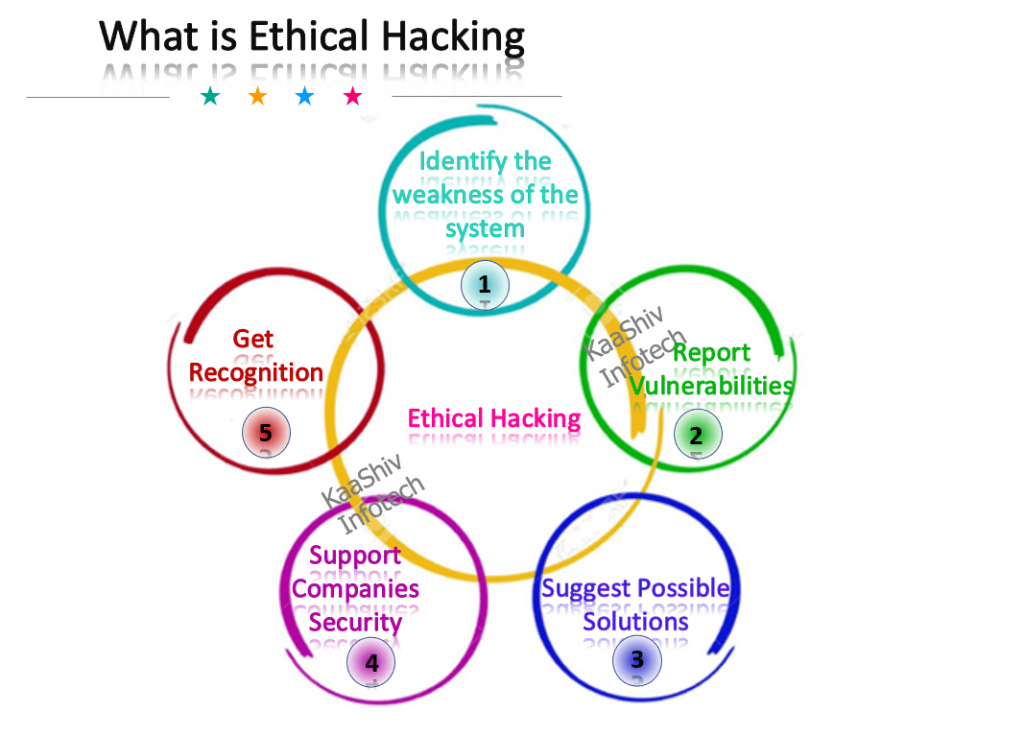
What is ethical hacking ?
- Ethical Hacking is when the individual is allowed to hacks the systems with the authorization to the stock owner to search out of weakness in an exceedingly system and the later fix them.
What are the types of ethical hackers ?
- Grey Box hackers
- Black Box penetration Testers
- White Box penetration Testers
What is IP address and Mac address ?
- IP address : To every device to an IP address is allocated, so that device can be located to the network.
- MAC (Machine Access Control) address : A MAC address is the unique serial number allocated to the each network interface on each device.
What is the DOS (Denial of service) attack ?
- Denial of Service, is a malicious attack on network that is complete by overflowing the network with unusable to traffic. Though, DOS does not cause any theft of the data or security breach, it can cost the website owner is great deal of money and time.
What are the common forms of the DOS attack ?
- Buffer Overflow Attacks
- Smurf Attacks
- Viruses
- SYN Attacks
- Teardrop Attacks
What is SQL injection ?
- SQL injection techniques used to steal data from the organizations, it is a fault to create in the application code. SQL injection happens to when you inject the content into an SQL query string and the output mode of content into a SQL query string, and the result modifies the syntax of your query in the ways you did not mean.
What are the types of computer based on social engineering attacks ?
Computer based social engineering attacks is,
- Phishing
- Baiting
- Online scams
List out common tools used by Ethical hackers ?
- MetaSploit
- WireShark
- NMAP
- Maltego
What is Phishing ?
- Phishing method includes sending of false emails, chats or website to the copy real system with aim of stealing data from the original website.
What are the advantages and disadvantages of hacking ?
Advantages
- It can be used to stop security attacks
- To plug the bugs and loopholes
- It helps to prevent data theft
- Hacking prevents malicious attacks
Disadvantages
- It makes massive security issues
- Get illegal system access
- Stealing private information
- Violating privacy regulations
What is the Burp Suite ?
- It is an integrated platform used for the attacking web applications. It contains of all the Burp tools a mandatory for attacking an application. Burp Suite tool has to same approach for the attacking web applications like framework for handling HTTP requests, upstream proxies, alerting, logging and so on.
Difference between hacking Vs. Ethical Hacking ?
- Hacking: It defines the banned way of accessing the system (Unauthorized Access)
- Ethical hacking: Official way of accessing the system (Penetration testing)
Why ethical hacking ?
- To find errors and vulnerabilities
- To determine the risk to the organization
What are the types of penetration testing ?
- Black box: No previous knowledge of network
- White box: Knowledge of remote network
Name top 10 vulnerability
- Injection
- Broken Authentication
- Sensitive data exposure
- XML External Entities (XXE)
- Broken Access control
- Security misconfigurations
- Cross Site Scripting (XSS)
- Insecure Deserialization
- Using Components with known vulnerabilities
- Insufficient logging and monitoring
What is CSRF (Cross Site Request Forgery)? How you can prevent this ?
- CSRF is an attack from a malicious website that will send a request to a web application that a user is previously authenticated against from a different website. To prevent CSRF you can add random challenge token to each request and associate them with user’s session. It makes sure the developer that the request received is from a valid source.
What is the Network Sniffing ?
- Network Sniffing method is used to monitors data flowing over the computer network links. By allowing you to capture and view the packet to level data on your network, sniffer tool can help you to the find network problems. Sniffers can be used for both stealing data off the network and also for genuine network management.

