network security projects – Kernel Hijacked information Monitoring using Server Stack Technique
Request for Project – [email protected] ; [email protected] ;[email protected]
Contact Number – 7667668009 / 7667664842
Whatsapp Number – 7667668009 / 7667664842
For complete project lists – final year project for cse
For internship – internship in chennai & inplant training in chennai
ABSTRACT:
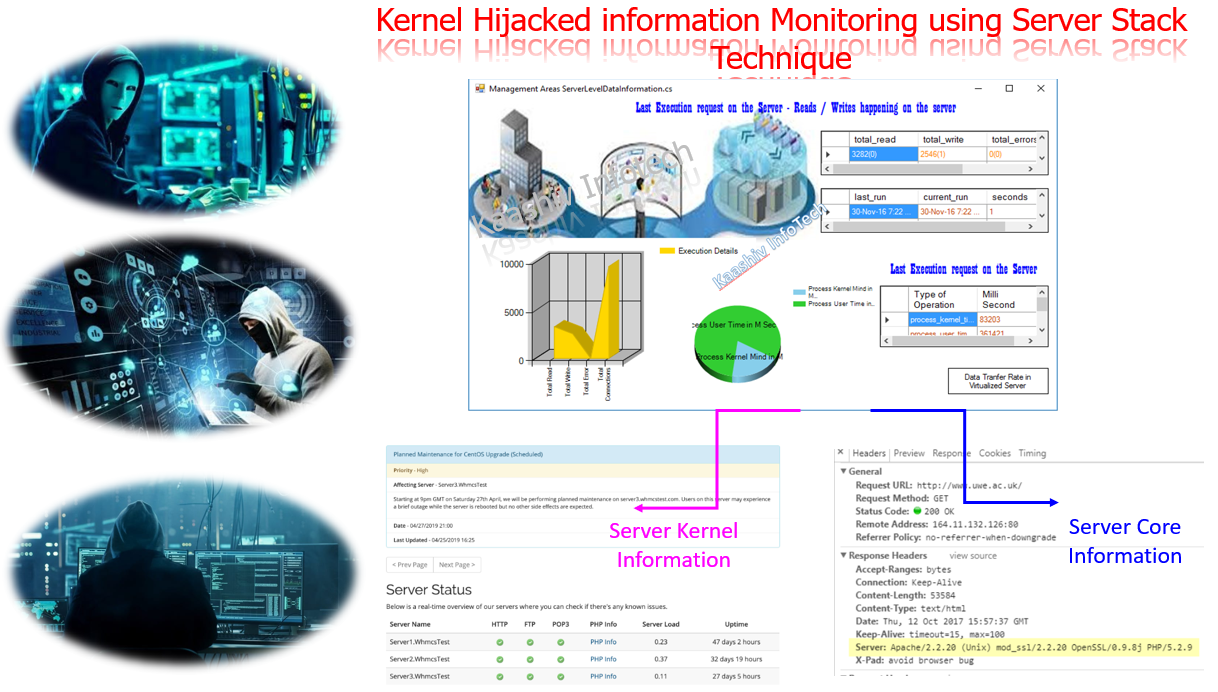
Inspecting communication between the client-server in turn snooping in your own application to penetrate into the network to extract information for good means is a challenging task in the current IT setup. Generation 1 System focuses on Telnet kind of operations which will take care of remote execution process. Security visualization is one of the major areas where most of the research is going on in visualizing the network nature for the systems. Due to vulnerability attacks and projection matrix manipulation. Many researchers are directed towards security monitoring measures and preventive techniques against intrusions. There are many major techniques and technological jargon dominating the security related stuffs in the IT industry. Many companies are focusing towards projecting their monitoring products in this evolving field. The goals of the optimization algorithm begin with: minimize running cost, for example (but not restricted to) power consumption; guarantee QoS for every class of application user (we predicted average predicted user response time) satisfy constraints on memory and scale-out (the number of instances of each task); In our project, our focused areas include host/server monitoring in an integrated based environment with specific features like internal and external monitoring, port activity and attack patterns. Important area to focus in this kind of Set Mon system involves, for a task, its number of threads, for a driver task like User Class involves the number of users for a processor, the number of cores
Existing system :
- Exiting system focuses only on cloud servers, we go ahead in deal with any kind of distributed servers, Parallel computing servers, cloud servers and grid servers too. It widely focused on foremost technical insights for our network visualization areas concentrating towards the Endpoint Connectivity -Host / Server Monitoring.
- Connectivity with the host and server will be monitoring for any downfall time, Utilization of the system – details about the host vs server utilization & Number of accessible users – Calculating the individual and concurrent users on the system has been monitored in network level specification.
- Apart from this our existing system focuses on the concept of Logging Packet Traces ,where the tracing of the packets traversing between the systems will be notified. Server logs information such as network level monitoring the security and application logs in the server has been traced in network. To learn more on networking, prefer ccna course or ccna internship or ccna training in chennai
Proposed system :
- Number of reported error in the server , Authentication information’s & Disabled services in the server have been identified for the security enhancement in network visualization
- In our system, we are trying to project the detailed view of how the problem occurred and possible solution for the servers.
- Intrusion related information’s were considered and precautionary measures towards intrusions will be addressed in our future work
SOFTWARE REQUIREMENTS
Platform : DOTNET (VS2010) – dotnet internship or dotnet training in chennai or dotnet course
Dot net framework 4.0
Database: SQL Server 2008 R2
HARDWARE REQUIREMENTS
Processor : Core 2 duo
Speed : 2.2GHZ
RAM : 2GB
Hard Disk : 160GB
PROPOSED SYSTEM ALGORITHM :
- The Push based monitoring algorithm is a different way to obtain the information is when monitoring initiative comes from the network devices.
- Push Based Monitoring Algorithm is used to perform aggregate queries in network traffic in all the cases of user level, security level, hard disk level.
- Apart from that Security events & User contact details in the network traffic must have to monitor the network visualization effectively to determine the set of flows whose size changes significantly from one period to another.
In case of learning these technologies, you can opt for
- Internships like ethical hacking internship , ethical hacking internships or hacking internship or cyber security internships
- trainings can be like hacking training in chennai , hacking course or ethical hacking course in chennai or cyber security training in chennai or cyber security course in chennai
- Inplant training can be hacking inplant training , cyber security inplant training
network security projects – Screenshots :
Request for Project – [email protected] ; [email protected] ;[email protected]
Contact Number – 7667668009 / 7667664842
Whatsapp Number – 7667668009 / 7667664842
For complete project lists – final year project for cse
For internship – internship at chennai & inplant training in chennai