cyber security projects for final year – Server Hacking – IP Address Grabber cum PC scrutinize Project
ABSTRACT:
It is used for hacking the IP Address of the particular system. A computer network is a set of devices connected through links. A node can be computer, printer, or any other device capable of sending or receiving the data. The links connecting the nodes are known as communication channels. Computer Network uses distributed processing in which task is divided among several computers.An Internet Protocol address (IP address) is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: host or network interface identification and location addressing. Network administrators assign an IP address to each device connected to a network. Such assignments may be on a static (fixed or permanent) or dynamic basis, depending on network practices and software features.
Request for Project – [email protected] ; [email protected] ;[email protected]
Contact Number – 7667668009 / 7667664842
Whatsapp Number – 7667668009 / 7667664842
For complete project lists – final year project for cse
For internship – internship at chennai & inplant training in chennai
INTRODUCTION:
It is used for hacking the IP Address ( cyber security projects for final year ) of the particular system. An Internet Protocol address (IP address) is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: host or network interface identification and location addressing. This is one of the best, cyber security projects for final year
Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998 IPv6 deployment has been ongoing since the mid-2000s.
IP addresses are written and displayed in human-readable notations, such as 172.16.254.1 in IPv4, and 2001:db8:0:1234:0:567:8:1 in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., 192.168.1.15/24, which is equivalent to the historically used subnet mask255.255.255.0.
The IP address space is managed globally by the Internet Assigned Numbers Authority (IANA), and by five regional Internet registries(RIRs) responsible in their designated territories for assignment to local Internet registries, such as Internet service providers and other end users. IPv4 addresses were distributed by IANA to the RIRs in blocks of approximately 16.8 million addresses each, but have been exhausted at the IANA level since 2011. Only one of the RIRs still has a supply for local assignments in Africa.Some IPv4 addresses are reserved for private networks and are not globally unique.
Network administrators assign an IP address to each device connected to a network. Such assignments may be on a static (fixed or permanent) or dynamic basis, depending on network practices and software features.
A computer network is a set of devices connected through links. A node can be computer, printer, or any other device capable of sending or receiving the data. The links connecting the nodes are known as communication channels. To learn more on networking, prefer ccna course or ccna internship or ccna training in chennai Computer Network uses distributed processing in which task is divided among several computers. Instead, a single computer handles an entire task, each separate computer handles a subset.
- Security in – cyber security projects for final year : It provides limited interaction that a user can have with the entire system. For example, a bank allows the users to access their own accounts through an ATM without allowing them to access the bank’s entire database.
- Faster problem solving in – cyber security projects for final year : Multiple computers can solve the problem faster than a single machine working alone.
- Security through redundancy – cyber security projects for final year : Multiple computers running the same program at the same time can provide the security through redundancy. For example, if four computers run the same program and any computer has a hardware error, then other computers can override it.
Features of Network
Communication Speed
Network provides us to communicate over the network in a fast and efficient manner. For example, we can do video conferencing, email messaging, etc. over the internet. Therefore, the computer network is a great way to share our knowledge and ideas.
File Sharing in cyber security projects for final year
File sharing is one of the major advantage of the computer network. Computer network provides us to share the files with each other.
Backup and Roll Back is Easy
Since the files are stored in the main server which is centrally located. Therefore, it is easy to take the back up from the main server.
Software and Hardware Sharing
We can install the applications on the main server, therefore, the user can access the applications centrally. So, we do not need to install the software on every machine. Similarly, hardware can also be shared.
Security in cyber security projects for final year
Network allows the security by ensuring that the user has the right to access the certain files and applications.
Scalability in cyber security projects for final year
Scalability means that we can add the new components on the network. Network must be scalable so that we can extend the network by adding new devices. But, it decreases the speed of the connection and data of the transmission speed also decreases, this increases the chances of error occurring. This problem can be overcome by using the routing or switching devices.
Reliability in cyber security projects for final year
Computer network can use the alternative source for the data communication in case of any hardware failure.
PHP
PHP is a popular language and contains many features. Some of those features are common as that are provided by many programming languages like C, C++, Perl and more. Also, PHP contains unique features of its own. In this article, we are going to list some of the unique features of PHP. – To learn php you are can prefer
Features:
Cross Platform Compatibility – It is used to create the desktop application by using advanced PHP features.
variable variables – PHP allows changing the variable name dynamically by using variable variables.
Real-Time Access Monitoring – PHP provides access logging by creating the summary of recent accesses for the user.
Error Reporting– It has some predefined error reporting constants to generate a warning or error notice. For example, when E_STRICT is enabled, a warning about deprecated methods will be generated.
XAMPP FRAMEWORK:
XAMPP is a free and open-source cross-platform web server solution stack package developed by Apache Friends, consisting mainly of the Apache HTTP Server, MariaDB database, and interpreters for scripts written in the PHP and Perl programming languages.
Since most actual web server deployments use the same components as XAMPP, it makes transitioning from a local test server to a live server possible.
XAMPP’s ease of deployment means a WAMP or LAMP stack can be installed quickly and simply on an operating system by a developer. With the advantage a number of common add-in applications such as WordPress and Joomla! can also be installed with similar ease using Bitnami.
Features of XAMPP Framework
XAMPP is regularly updated to the latest releases of Apache, MariaDB, PHP and Perl. It also comes with a number of other modules including OpenSSL, phpMyAdmin, MediaWiki, Joomla, WordPress and more.
Self-contained, multiple instances of XAMPP can exist on a single computer, and any given instance can be copied from one computer to another.
Features of MYSQL
Relational Database Management System (RDBMS): MySQL is a relational database management system.
Easy to use: MySQL is easy to use. You have to get only the basic knowledge of SQL. You can build and interact with MySQL with only a few simple SQL statements.
It is secure: MySQL consist of a solid data security layer that protects sensitive data from intruders. Passwords are encrypted in MySQL.
Client/ Server Architecture: MySQL follows a client /server architecture. There is a database server (MySQL) and arbitrarily many clients (application programs), which communicate with the server; that is, they query data, save changes, etc.
Free to download: MySQL is free to use and you can download it from MySQL official website.
It is scalable: MySQL can handle almost any amount of data, up to as much as 50 million rows or more. The default file size limit is about 4 GB. However, you can increase this number to a theoretical limit of 8 TB of data.
Compatibale on many operating systems: MySQL is compatible to run on many operating systems, like Novell NetWare, Windows* Linux*, many varieties of UNIX* (such as Sun* Solaris*, AIX, and DEC* UNIX), OS/2, FreeBSD*, and others. MySQL also provides a facility that the clients can run on the same computer as the server or on another computer (communication via a local network or the Internet).
Allows roll-back: MySQL allows transactions to be rolled back, commit and crash recovery.
High Performance: MySQL is faster, more reliable and cheaper because of its unique storage engine architecture.
High Flexibility: MySQL supports a large number of embedded applications which makes MySQL very flexible.
High Productivity: MySQL uses Triggers, Stored procedures and views which allows the developer to give a higher productivity.
HARDWARE REQUIREMENTS
- System : Intel inside i3
- System Type : 64-bit Operating System
- Storage :500GB
- RAM :4 GB
SOFTWARE REQUIREMENTS
- Operating system : Windows 10
- Front End : PHP
- IDE :Xampp
- Data Base : MYSQL
In case of learning these technologies, you can opt for
- Internships like ethical hacking internship , ethical hacking internships or hacking internship or cyber security internships
- trainings can be like hacking training in chennai , hacking course or ethical hacking course in chennai or cyber security training in chennai or cyber security course in chennai
- Inplant training can be hacking inplant training , cyber security inplant training
SAMPLE CODE:
<?php
require “config.php”;
// this code is written by wikitechy company
//whether ip is from share internet
if (!empty($_SERVER[‘HTTP_CLIENT_IP’]))
{
$ip_address = $_SERVER[‘HTTP_CLIENT_IP’];
}
<!–====== Jqueryjs ======–>
<script src=”assets/js/vendor/jquery-1.12.4.min.js”></script>
<script src=”assets/js/vendor/modernizr-3.7.1.min.js”></script>
<!–====== Bootstrap js ======–>
<script src=”assets/js/popper.min.js”></script>
<script src=”assets/js/bootstrap.min.js”></script>
<!–====== Slick js ======–>
<script src=”assets/js/slick.min.js”></script>
<!–====== Magnific Popup js ======–>
<script src=”assets/js/jquery.magnific-popup.min.js”></script>
Request for Project – [email protected] ;
Contact Number – 7667668009 / 7667664842
For complete project lists – final year project for cse
For internship – internship in chennai
Screenshots:
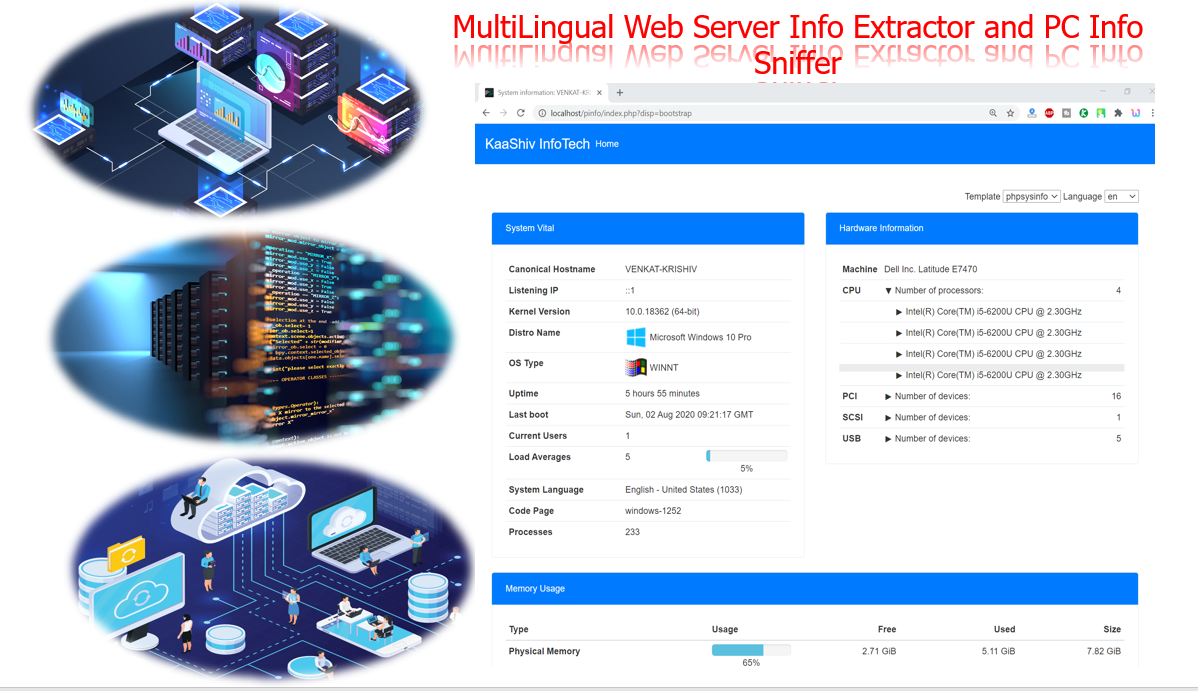
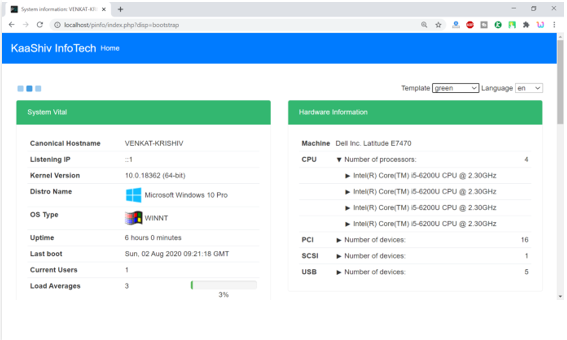
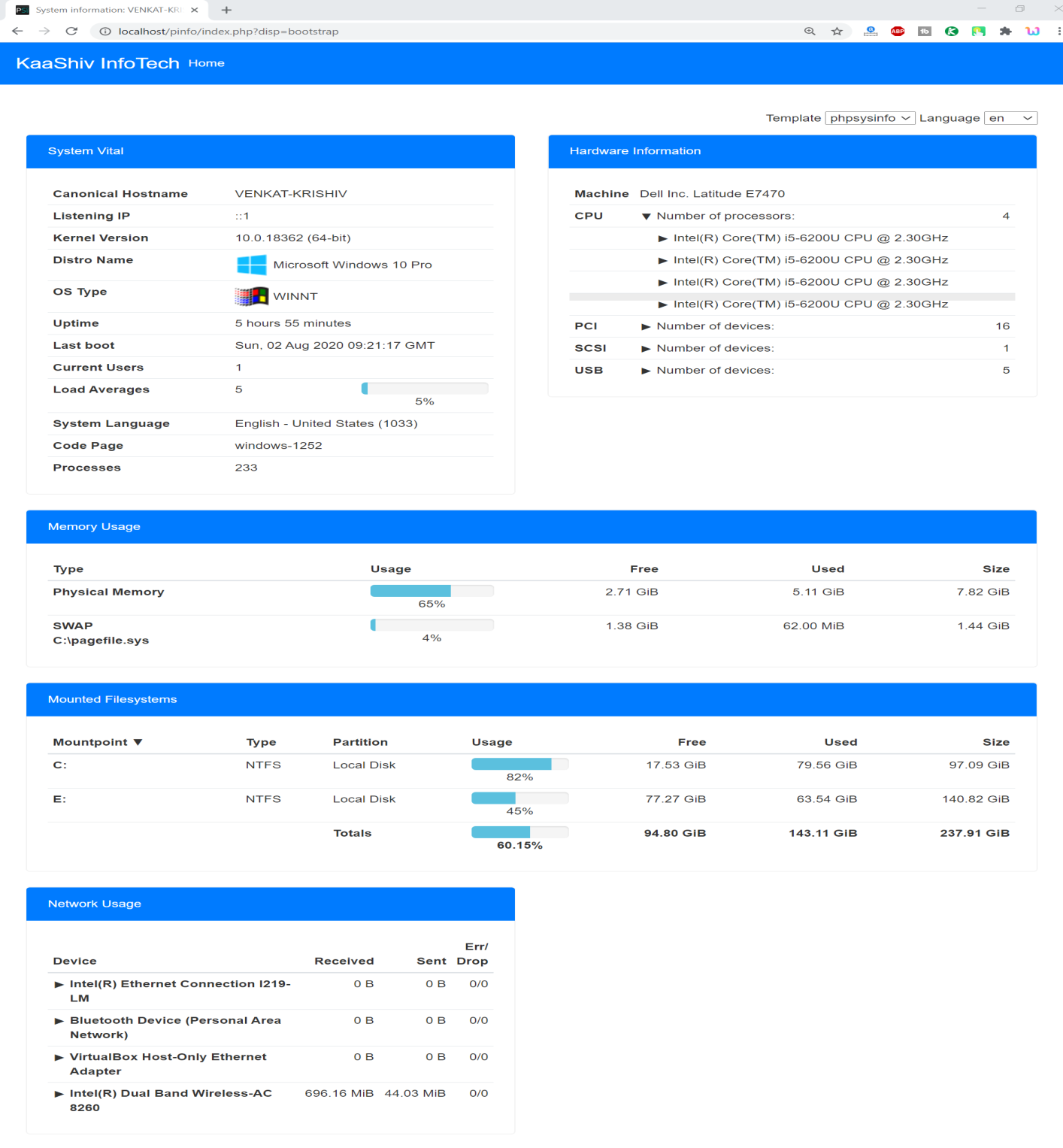
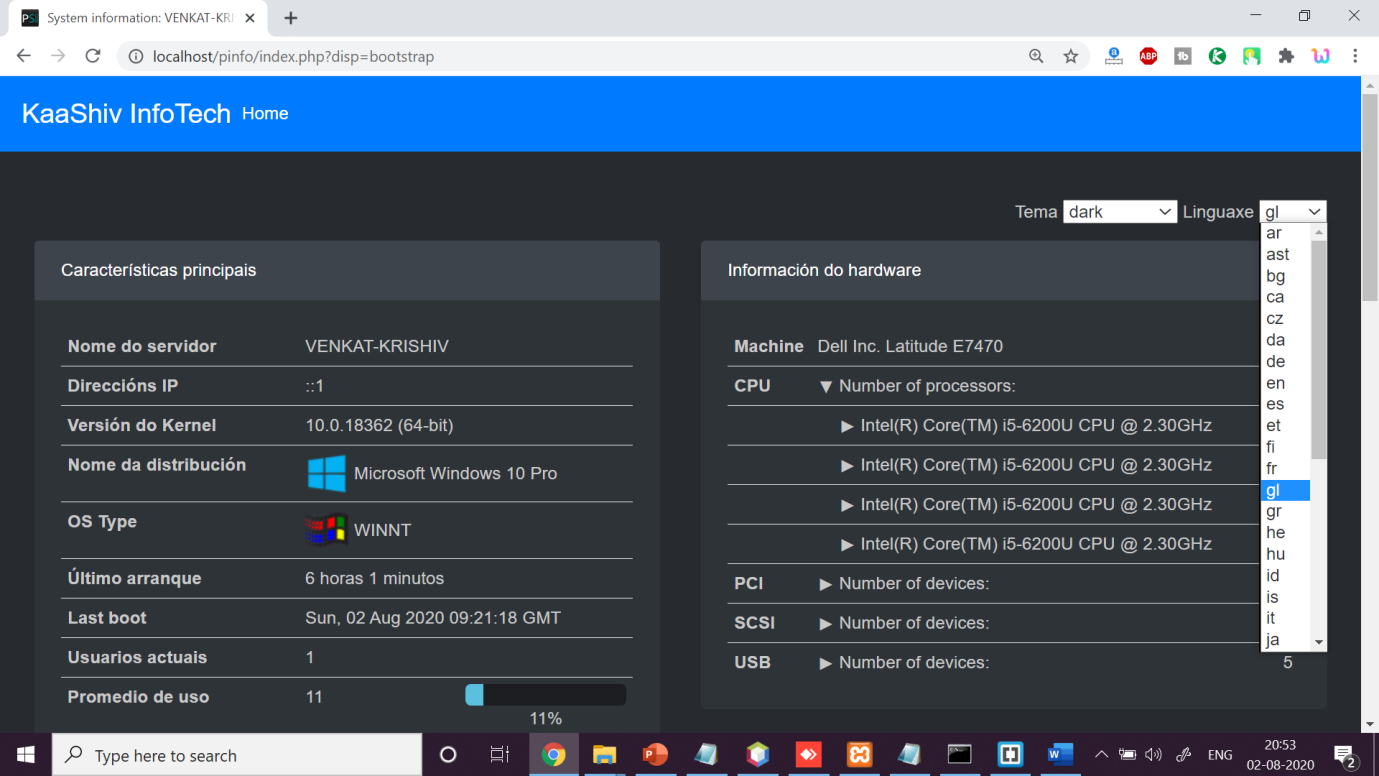
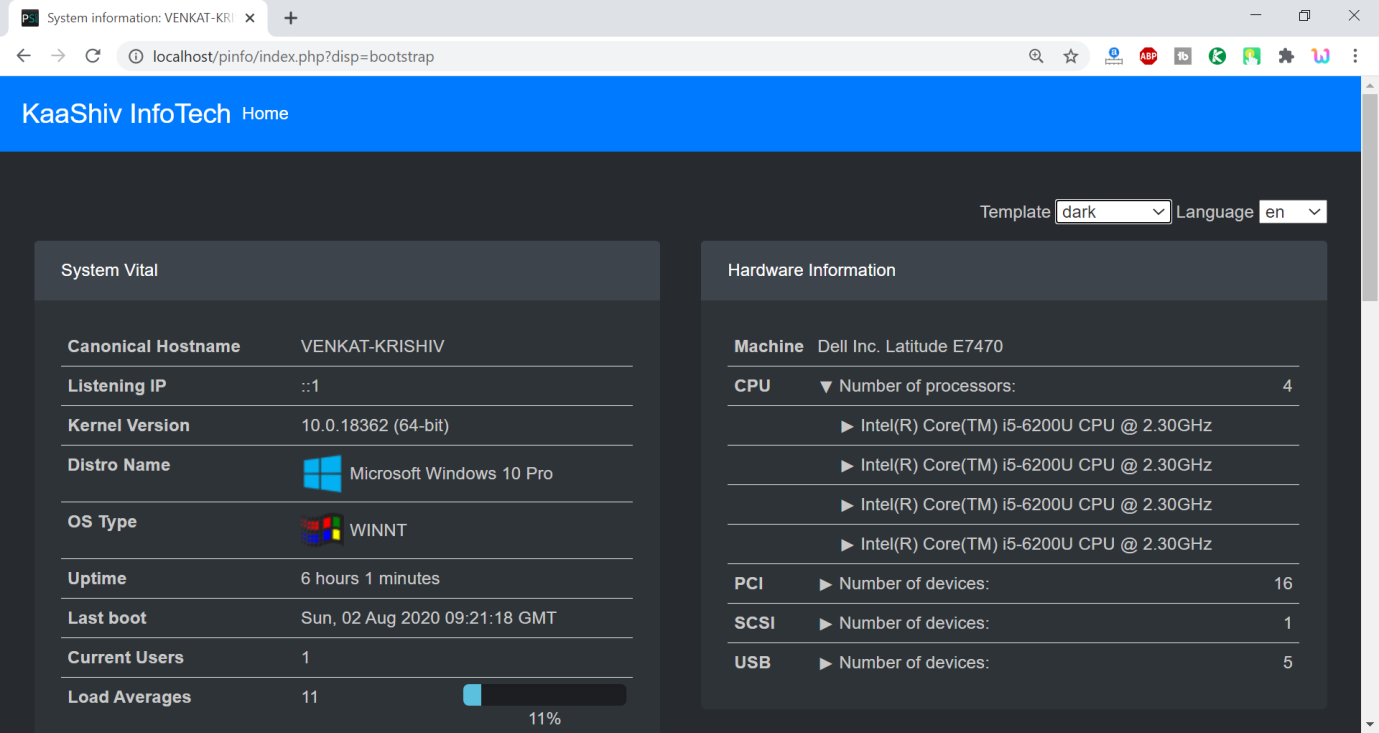
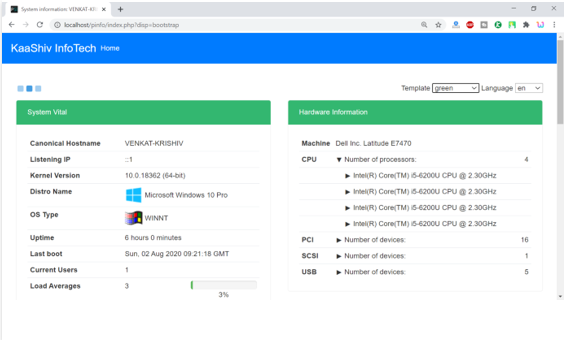
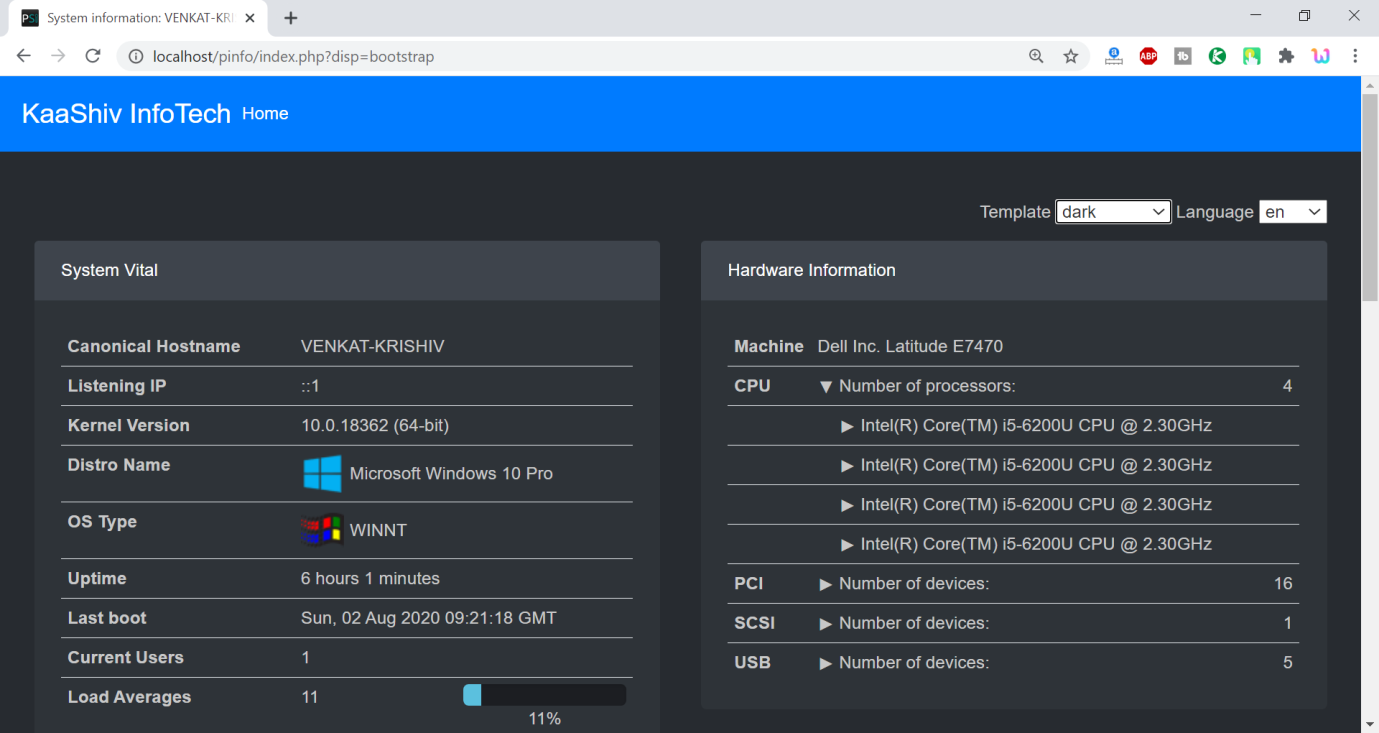
cyber security projects for final year
Request for Project – [email protected] ; [email protected] ;[email protected]
Contact Number – 7667668009 / 7667664842
Whatsapp Number – 7667668009 / 7667664842
For complete project lists – final year project for cse
For internship – internship at chennai & inplant training in chennai