
ISO Certified Company - Google Rated Number 1
cyber security course in chennai
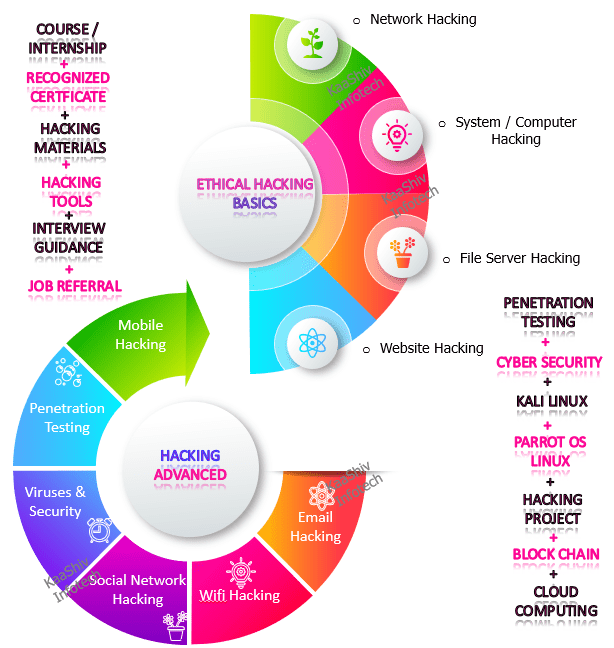
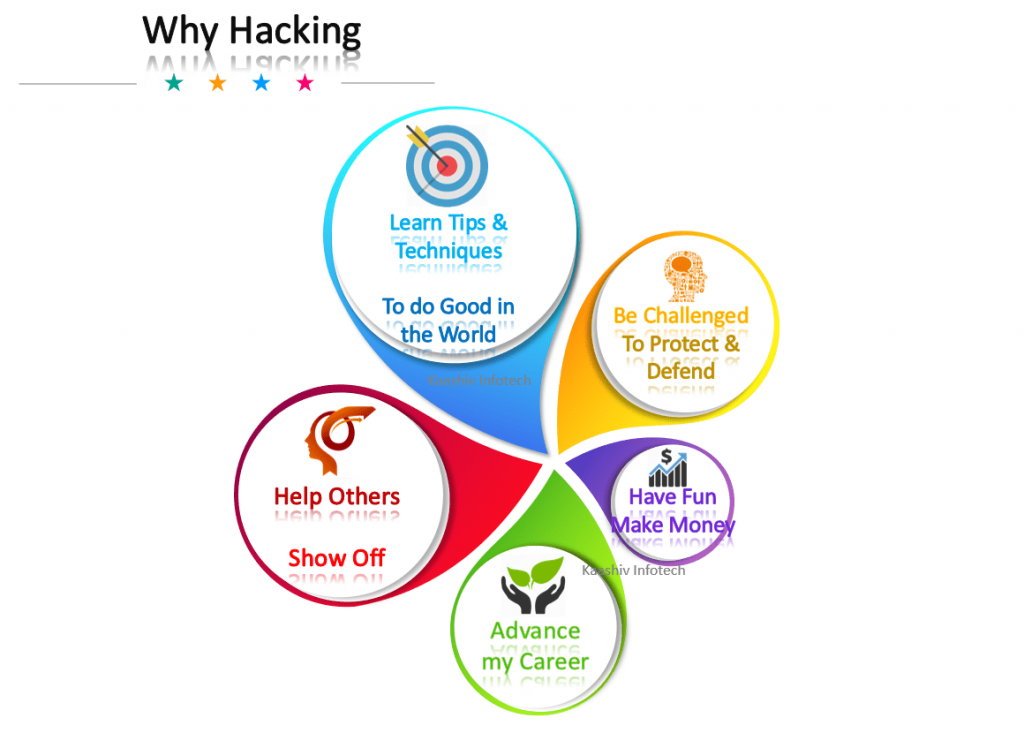
KaaShiv Infotech offers, cyber security course in chennai . Course provides you an in-depth knowledge of Cyber Security. This course enables the students to understand and learn the current trend in the job market. Students will prefer online courses to build their profile for their jobs and also for their higher studies. Our company provides both offline and online courses cyber security . cyber security and ethical hacking course in chennai – imparts technical and programming skills on the below list of hacking areas such as,
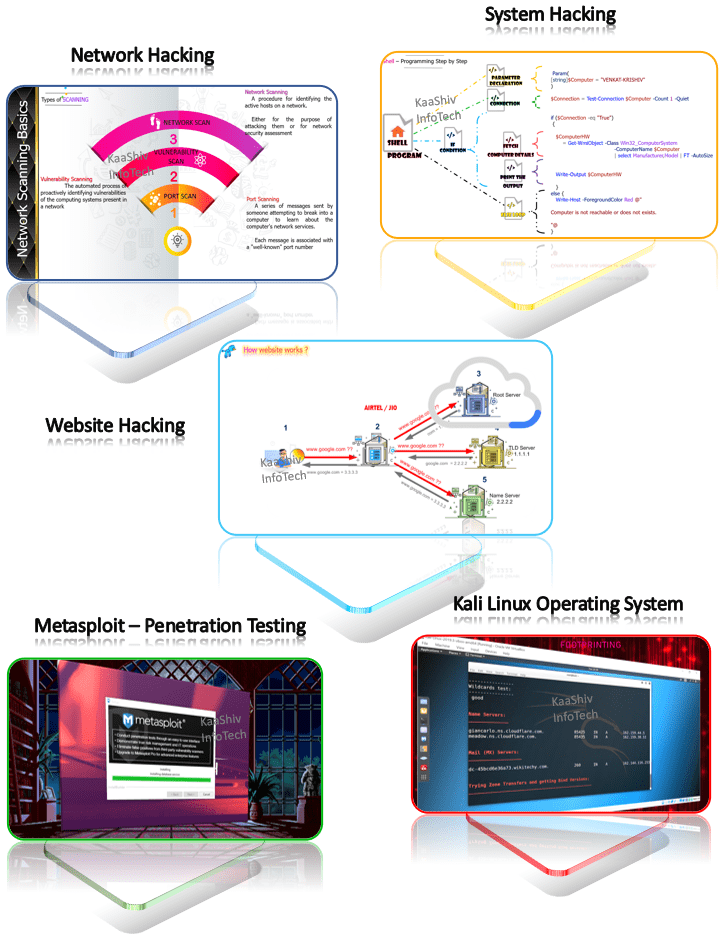
- Network Hacking
- Command Shell Hacking
- System Hacking
- File Server Hacking
- Web Server Hacking
- Website Hacking
- Mobile Hacking
- Penetration Testing
- Social Network Hacking
- Email Hacking
- Wifi Hacking
Highlights of our company
- Common Wealth Bank Recognized Leading Light Rising Star Award Winner
- Run by 10 Years Microsoft Awarded MVP ( Most Valuable Professional )
- Google Recognized Experts and Cisco Recognized Certified Experts
- Microsoft Certified Professionals
- Artificial Intelligence and Robotics Experts
cyber security course in chennai tamilnadu
Why our company provides, cyber security training centre in chennai
The Course curriculum for, cyber security degree course in chennai – is carefully researched and prepared by professionals from MNC to meet the demands expected in the current IT industries. After completing, Cyber security course in chennai at KaaShiv Infotech, students will be familiar with the entire ethical hacking, cyber security, Implementing a hacking project. Below are some insights of our program, cyber security analyst course in chennai ,
Trainers to train you
Our, cyber security course in tamilnadu (or) Cyber security course in chennai – Trainers are real-time IT experts and cyber security professionals worked in leading MNCs like
- TCS,
- HCL,
- Infosys,
- Cognizant,
- Wipro

Cyber security course in chennai - Online
- Learn Cyber Security Online – kaashiv offers training on cyber security online or Cyber security course in chennai – for the students or professionals who prefer, cyber security course work from home .
- Cyber Security intern will be learning cutting edge technology based on cyber security online classes .
- Our, cyber security online course programme provides Online portal to study anytime, online classes to study flexibly , industry recognized certificate with, cyber security internship questions (or) interview questions for cyber security course – for all the attendees.
- Most of the students will be getting ready for campus placement or off campus interviews.
- Applying basic theoretical ideas into the real world via internship programs horne their skills to the next level of industrial knowledge.

cyber security courses and jobs
Online Course Training provides a real-time exposure for the students on the latest and trending technologies in the software companies. Below are some Top jobs in IT Industry with very good,
- Network administrator/manager
- Penetration tester
- Web security administrator/manager
- Data security analyst/specialist
- Cyber Security Trainee/Cyber Operations specialist
- Ethical Hacking specialist
- IT Analyst – Vulnerability Management
- Ethical Hacking Application Developer
KaaShiv Infotech course program ( Cyber security course in chennai ) horne you in the above said skills / job roles from basics to advanced.
cyber security course in chennai with placement
Course Training to the Students / courses for cyber security
Learn and Implement
45 Concepts Covering 7 Technologies
+ 1 Projects
Cyber Security Course Syllabus
- Courses on cyber security – Duration: Week Day / Week End – Any Day Any Time – Students can come and study
- Training hours: 50 hrs
- Software & other tools installation Guidance
- Hardware support
- Cyber Security Course Materials creation / Cyber Security Project Report creation
- KaaShiv Infotech is top under, ethical hacking and cyber security course in chennai , based 1 real time projects
- Certificates will be given
- Course Completion Certificate
- Industrial exposure certificate
- + ( Achievement certificate for best performers )
- cyber security training with job guarantee in chennai – After 6 months of regular Paid course, Course becomes free + For best interns Stipend will be provided + Best Interns will be offered Job too.


S.No |
network security training in chennai100% Practical – Live HandsOn – introduction to cyber security syllabus |
|---|---|
| Topic 1 : | Ethical Hacking Basics ( Introduction Hacking , Job Openings, Mega Breach History , Hacking Terminologies , Elements of Information Security, Motives of Information Security, Information Security Threats Categories , Hacker Classes , Website Info Extraction , Penetration Testing , Bot Website , Website Directory Extraction , SQL injection , Hacking Social Data ) |
| Topic 2 : |
Network Hacking
|
| Topic 3 : |
Command Shell Hacking
|
| Topic 4 : |
System Hacking
|
| Topic 5 : |
File Server Hacking
|
| Topic 6 : | Web Server Hacking ( What is Root Name Server , How website works ? , How website works ? , How DNS Works , How Dig Tools Works , Server Info Extraction Tool – Part 1 , Server Info Extraction Tool – Part 2 – DNSKEY , Server Info Extraction Tool – Part 2 – DS Record , Anatomy of a Website , How Internet Works , How Website Works , NSLookup Networking Command , Diggint Tool , How to make a Server ? , Server into a Web Server ? , Web Server to World Wide Web Registered Server ) |
| Topic 7 : | Website Hacking ( Information Gathering – FootPrinting , DNS Enumeration , DNS Info Extraction , What is DNS , What is Reverse DNS , Chrome Extension , IP Information of the Website , SPF Record Details , Web Server Information , Website Owner Information , Termux ReconDog , Install Python&GIT , Port Scanning , Who is Lookup , Who is Lookup with software , Who is Lookup with websites , Port Scanning , Honey Pot Server , Reverse IP Lookup , Reverse IP Lookup with websites , Censys – Website Monitor tool , What is Web Session ? , What is Session Hijacking ? , Tor Browsers , Anonymizers , Type of Anonymizers , Anonymizers – Bypass Web Filters , Anonymizers – Bypass Internet Traffic , What is Phishing , Phishing Prevention , What is IP Spoofing , How IP Spoofing works ? , IP Spoofing Basics – How it works ? , IP Spoofing types , IP Spoofing Types – Non-Blind Spoofing , IP Spoofing Types – Blind Spoofing , IP Spoofing Types – Smurf Attack , IP Spoofing Types – MITM Attack , IP Spoofing with Software’s , IP Spoofing with Websites , What is MAC Spoofing , Remote Access VPN , How VPN protocol works ? , VPN Data Encryption , PC VPN Settings , Mobile VPN Settings , IP Spoofing with VPN , How to get Current Ip address ? , Secret mobile Settings for VPN configuration , VPN network configuration with new IP , What is VPN , What is Firewall – Technical Info , IP Spoofing Prevention Technique , Additional Features of Firewall , Firewall Types , Host Based Firewall , How Router works ? , Network Based Firewall , What is Cloaking in Hacking ) |
| Topic 8 : | Mobile Hacking ( Find mobile number details , Access Mobile Number information , Basic Phone Info Package , Install Termux , Access Memory using Termux , Hacking Mobile Task Manager , Networking Cmds in Termux , Ping Command in Termux , Botting Websites , What is an Internet Bot ? , What is a Website Bot ? , What is a BotNet ? , How Hackers attack Website – DOS Attack , How DDOS works , Charter – AntiBot Scanner , Microsoft Safety Scanner , Website Directory Extraction , What is Web Server , Vulnerability testing , Website Vulnerability Analysis ) |
| Topic 9 : | Penetration Testing ( MetaSploit – PenTest Tool , What is MetaSploit , MetaSploit History , MetaSploit Packages , MetaSploit Modules , MetaSploit Sub Modules , How MetaSploit works with Pen Testing , How Exploits works in Metasploit ? , Metasploit Architecture , Metasploit Library , Metasploit Codes , Metasploit Tools , Metasploit Command Basics , Modules in Metasploit , Create and Setup Exploit, Attack Target , Fetch the injected Virus Path , Make Directory to Control Target , Injecting Files in to the Target Machine , Idle time and IP Details of the Target , Keyboard Hacking/Password Attacks , Audio Recording , Hacking Screenshot of Target , Hacking Screen of the Target , Hack Camera Details in the Target , Hack Camera Take snap of the Target , Hack Camera Take Live Video of the Target , How to install Metasploit in Mobile , How to search Metasploit packages , Find open ports using Metasploit in target ) |
| Topic 10 : | Social Network Hacking ( find fb id , Find facebook friends using termux – Facebook Tricks ) |
| Topic 11 : | Email Hacking ( Email Spoofing , Mail Tracking with gmail , Send mail to find location ) |
| Topic 12 : | Wifi Hacking ( Wifi Introduction – Basic components of Wifi , How Wifi works , Wireless Devices, Get Basic Wifi Accounts Stored in the Computer , Get Wifi interfaces Stored in the Computer , Get Wifi Properties Stored in the Computer , How to Export Wifi Passwords , How to get Windows Wifi Password ) |
| Topic 13 : | Kali Linux – Hacking Operating System ( Introduction , FootPrinting Tools, Backdoor Attack Tools , Reconnaisance Tools , Sniffing Tools ) |
| Topic 14 : | Parrot OS – Hacking Operating System ( Anonymous Access – Be a Hacker , No one can hack you , Control your network usage , Control your computer Execution , Control anyone in the Network ) |
+ Course Completion Certificate
+ Free Industrial exposure certificate + (Achievement certificate for best performers) + 1 Cyber Security Projects
Ethical Hacking training in chennai
Apply for course - Contact Us
cyber security course with placement - After 6 months of regular Paid course, Course becomes free + For best interns Stipend will be provided + Best Interns will be offered Job too.
Contact Number / Whatsapp Number
Mobile 2 : 7667664842
Mobile 3 : 9840678906
ethical hacking course in chennai
Sample Video – Cyber Security Training Courses in Chennai
Cyber Security Course in Chennai – Demo Link :
Check out our Sample Content under the topics ” hacking course in chennai & cyber forensics courses in chennai “
Check our Previous testimonials from students from Different Countries and Different States :
Check our students, Internship feedback kaashiv infotech reviews
More about our Company
hacking course in chennai
Our, diploma in cyber security course in chennai - Training Youtube Channels –
Our Technology Channel :
https://www.youtube.com/channel/UC2MYZHG8a56u4REI2RedtRA
Our Subject Channel :
https://www.youtube.com/channel/UC9dcBYLL-ZGTy7ml8YMTlag/videos
Check out the colleges attended our Internship :
Click to view more details cyber security course reviews
Intern Students Feedback
Check our ( Intern )Students Feedback :
Inplant training in chennai for Cyber Security – Feedback – https://www.kaashivinfotech.com/inplant-training-feedback
Cyber Security Internship – Feedback – interns for cyber security students
Our Live Project:
We ranked Top 2000 technological companies in India, www.wikitechy.com

YEARS OF EXPERIENCE COMPANY

PROFESSIONAL EXPERTS
/ TRAINERS

SUCCESSFUL COMPLETED STUDENTS

COLLEGE
STUDENTS
PARTICIPATED
1. Materials for the course will be provided after the completion of the programme.
2. Regular tech updates to the students.
3. Free course Projects given
1. Industry Recognized, certificate for course will be given.
2. Certificates will be given ( Inplant Training Certificate & Industrial exposure certificate ) + (Achievement certificate for best performers)
2 day / 3/ 4 / 5 / 10, 20 days or 1 month to 6 Months ( Any Number of Days – Based on student preferences)
Specialized technologies from, cyber security course in chennai
information security management course in chennai
courses in cyber security
cyber security courses for beginners
- cyber security course for beginners – Cyber security entry level Course , can be done by the freshers to build their careers. This program will provide a clear baseline for the entry-level engineers to enter into the IT industry.
- Before entering into the companies, doing training will give you more clarity in the programming field.
- Kaashiv Infotech recommends all department students, fresher, and even school students to take up this online training and build their careers.
Cyber Security Courses for Experience candidate
- This training is designed for working professionals looking to pick up skills in advanced concepts in Cyber security.
- This course program covers Network Hacking, Web Server Hacking, Mobile Hacking, Wifi Hacking, etc. After completing this course , you can pursue careers in the cyber security industry, such as Penetration tester , Web security administrator/manager , Data security analyst/specialist , Cyber Security Trainee/Cyber Operations specialist and Ethical Hacking specialist
- Kaashiv infotech Offers,
- Cyber Security Courses for 1+ Experience Candidate
- Cyber Security Courses for 2+ Experience Candidate
- Cyber Security Courses for 3+ Experience Candidate
- Cyber Security Courses for 4+ Experience Candidate
- Cyber Security Courses for 5+ Experience Candidate
- And any year of experience people also can study
Cyber Security Courses for Non-technical Students
- This Course training can be done by the non-technical students to build their career
- A non-technical student can become a Cyber Operations specialist , in fact, many such non-technical students are Ethical Hacking specialists in several companies.
- First, You can start by watching YouTube videos and reading documentation and different blogs, practice regularly, and implement what you learn.
- Kaashiv Infotech recommends all non-technical backgrounds like marketing, business development, finance and sales etc.,
Cyber security Courses for School Students
- Cyber security is important progress of a school student
- It’s the desire of every programmer to learn ethical hacking. But, it’s hard to find the start and progress. Because there are lots of resources and courses and techs to learn on cyber security.
- Help students understand how the technology works with these design and development tools. Are your students interested in learning Cyber Security, then Kaashiv Infotech is the best company for Computing courses.
- Kaashiv infotech offers Cyber Security courses for,
- Secondary student
- Higher Secondary Student
- From 5th standard to 12th Standard students also can study
Cyber security Courses for Foreign students - Outside India
- Kaashiv offers online courses for foreign students or working professionals.
- Kaashiv infotech is the best company for online cyber security courses.
- Our Cyber security online portal to study anytime, online classes to study flexibly, industry-recognized certificate for all the attendees.
cyber security course questions and answers
Is cyber security a good career ?
-
Cyber security is really one of the newest job domains nowadays. According to a study conducted by the Global Information Security Network Study, nearly 2 million open cybersecurity jobs will be created by 2022. Even when it comes to salaries, professions requiring cyber security skills demand about 16 percent higher than similar non-security IT professions. So, yes, a cyber security career is a highly profitable and controlled for exponential growth in the near future.
What is the scope after completing Cyber Security course in Tamil Nadu ?
-
After completing a Cyber Security course, candidates who need to go for higher studies can study Postgraduate degree in:
- Penetration Testing and Vulnerability Analysis
- Applied Cryptography
- Digital Forensics
What is the average salary of a Cyber Security professional in Tamil Nadu ?
- Cyber Security professionals get an average salary package of around Rs 5-6 LPA over different companies.
What are the eligibility criteria for this cyber security course in Chennai ?
- Courses can be done by school students too. So, no need of degree for doing Courses.
- May have a non-programming background
- Are not compulsory to have prior work experience
What are the objectives of a cyber security course ?
- With a cutting-edge program, this cyber security course helps you build a foundation of cyber security concepts — from the basics to advanced levels. You will study about network hacking, mobile hacking techniques, and ways to defend against cyberattacks by designing, engineering, and managing the overall security posture of an organization. Through practical case studies, interactive quizzes, and industry projects, you will gain the practical skills you want to shine in this exploding field.
How to Avail Free online cyber security Course ?
- cyber security course free – After 6 months of regular Paid Course, Course becomes free + For best interns Stipend will be provided + Best Interns will be offered Job too.
How to study cyber security course after 12th ?
- cyber security eligibility / cyber security course eligibility – Courses can be done by school students too. So, no need of degree for doing Courses.
- Then you should go for a course to make you Ethical hacker
- Getting all the necessay training you will be certified as an ethical hacker on completion and many companies will hire you for IT security
- Go to this website for full detail on Ethical Hacking Course
How much does cyber security course cost ?
- If you’re interested in getting into cyber security, you know you’re going to need to learn a lot of information and pick up quite a few new skills. You can try to learn cybersecurity on your own, but for most people, getting access to training is the best way to go.
- If you need to know about the cyber security course cost you can contact our customer care 7667668009, or you can come office directly.
What is the syllabus for cyber security course ?
- cybersecurity syllabus (or) cyber security course content – is listed below
- Network Hacking
- Command Shell Hacking
- System Hacking
- File Server Hacking
- Web Server Hacking
- Website Hacking
- Mobile Hacking
- Penetration Testing
- Social Network Hacking
- Email Hacking
- Wifi Hacking
Can you learn cyber security online ?
- Learn Cyber Security skills online with Kaashiv . Kaashiv infotech is the world’s leading IT and cybersecurity online training network offering in-depth ethical hacking courses, for beginning, intermediate and advanced hacks.
Can I do cyber security from home ?
- There are few chances to work from home in cybersecurity such as cybersecurity research, security consultancy, audits, penetration testing, IAM analysis, security architects, etc. Due to the increased responsiveness of cybercrime, the request for specialists who can protect the business’s digital space is increasing quickly.
Why You Should Enrol for Online Course Program With Kaashiv InfoTech ?
- Learn from top Internship company
- Globally Accepted Degree
- Flexible learning – Anytime Anywhere Learning
- Preferred Destination for Corporate Hiring
What soft skills are needed for cyber security ?
- Strong Research and Writing Skills
- Collaboration
- Adaptability
- Networking
- Problem Solving
Is python needed for cyber security ?
- Python is a useful programming language for cybersecurity because it can achieve many cybersecurity functions, including malware analysis, scanning, and penetration testing functions. It is user-friendly and has an well-designed simplicity, making it the perfect language choice for several cybersecurity specialists.
Does cybersecurity need coding ?
The majority of entry-level cybersecurity jobs do not need coding skills. Though, being able to write and understand code may be essential in some mid-level and upper-level cybersecurity positions that you will become qualified for after you’ve built a few years of experience.
Is ethical hacking course worth it ?
- Cybersecurity specialists find work maintaining the security of networks and data for businesses and organizations.
- One of the main tasks of a cybersecurity specialist is to keep tabs on the systems employed by their organization and report any issues to management. They are also responsible for anticipating future threats and recommending how to deal with them.
How to - become a cybersecurity expert ?
Even though a job in cybersecurity can be highly satisfying, it can also be very interesting and stressful. Understanding some of the job responsibilities, as well as the features and nature traits of these jobs, may help you decide if a career in cybersecurity is right for you.
Which startups provide the best , cyber security courses 2021 India ? What are the duration of these trainings ?
- The Answer is, Kaashiv Infotech offers courses . This training involves, practical knowledge and real time experience . Course duration can be from 1 day to any number of days like 6 months. Usually students will prefer 5 days to 6 months of course
which is the best course for cyber security (or) which ethical hacking course is best ?
What are the requirements for cyber security course ?
- There are no specific degree requirements used as prerequisites for cybersecurity jobs. However, most managers will be looking for a bachelor’s degree in computer science, cybersecurity, or a related technical field.
cyber security course requirements
- Are enrolled in a degree program at the time of the course
- Have a cumulative GPA of 2.5 or above
- International students also have specific eligibility requirements.
Which is the best institute for - Online Cyber Security & Ethical Hacking course ?
- The Answer is, Kaashiv Infotech company is the best institute for online cyber security and ethical hacking course.
- For online course you can refer this link ethical hacking course ( https://kaashiv.com/internship/ethical-hacking-internship/ )(or) you can contact our customer care 7667662428 . our team will help you.
What do cyber security interns do ?
- This contains tasks like reading and responding to emails, establishing documents or other digital resources, studying and reviewing the company’s present IT policies, and researching new security products and strategies.
- In addition, cyber security interns may also take part in projects that are more specific to cyber security.
How to Describe Your Cyber Security Experience ?
cyber security internship job description for resume ( cyber security internship resume )
- Perform technical evaluation and penetration testing of internally- and commercially-developed applications (web, desktop, and mobile), systems, and medical devices.
- Support in developing the security controls for IT solutions of all types (mobile, web, client-server, etc).
- Maintain knowledge of security vulnerabilities, threats, and industry standard methodologies.
- Participate in suitable and relevant sessions and courses to maintain technical proficiency.
- Assist in developing and implementing an annual personal education plan to develop and maintain currency of security-related skills, technologies, methodologies, and standard methodologies.
How About, cyber security internship cover letter ?
cover letter for cyber security internship
- Start your Cyber security internship cover letter with a compelling opening statement.
- Tell them why you’re the perfect candidate to resolve their future cyber concerns.
- Clarify why this specific company and position are ideal for you.
- Close it with a call-to-action as simple-but-powerful as a brute-force attack.
Cyber Security Interview Questions and Answers
What is cybersecurity ?
- Cybersecurity denotes to the protection of hardware, software, and data from attackers. The main purpose of cyber security is to protect against cyberattacks like accessing, changing, or destroying complex information.
What are the elements of cybersecurity ?
- Information security
- Network security
- Operational security
- Application security
- End-user education
- Business continuity planning
What are the advantages of cyber security ?
- It protects end-users.
- It keeps the business against ransomware, malware, social engineering, and phishing.
- It gives protection for both data as well as networks.
- Cybersecurity stops unauthorized users.
- Increase recovery time after a break.
Define Cryptography
- It is a method used to protect data from third parties called adversaries. Cryptography allows the sender and receiver of a message to read its details.
What is a Firewall ?
- It is a security system designed for the network. A firewall is set on the limits of any system or network which monitors and controls network traffic. Firewalls are used to protect the system or network from viruses, worms, and ,malware. Firewalls also can prevent content filtering and remote access.
Name the different layers of the OSI model.
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
What is a VPN ?
- VPN stands for Virtual Private Network. It is a network connection method for making an encrypted and safe connection. This method protects data from intrusion, snooping, restriction.
What is CSRF (Cross Site Request Forgery)? How you can prevent this ?
- CSRF is an attack from a malicious website that will send a request to a web application that a user is previously authenticated against from a different website. To prevent CSRF you can add random challenge token to each request and associate them with user’s session. It makes sure the developer that the request received is from a valid source.
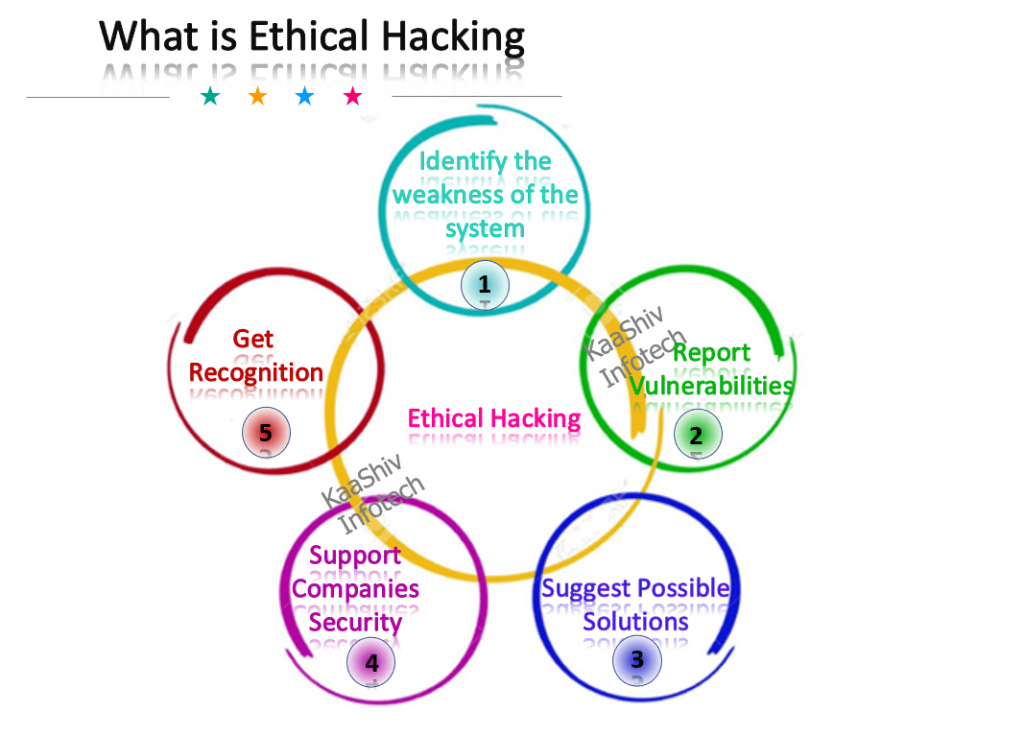
What is ethical hacking ?
- Ethical Hacking is when the individual is allowed to hacks the systems with the authorization to the stock owner to search out of weakness in an exceedingly system and the later fix them.
What are the types of computer based on social engineering attacks ?
Computer based social engineering attacks is,
- Phishing
- Baiting
- Online scams
What is the Network Sniffing ?
- Network Sniffing method is used to monitors data flowing over the computer network links. By allowing you to capture and view the packet to level data on your network, sniffer tool can help you to the find network problems. Sniffers can be used for both stealing data off the network and also for genuine network management.
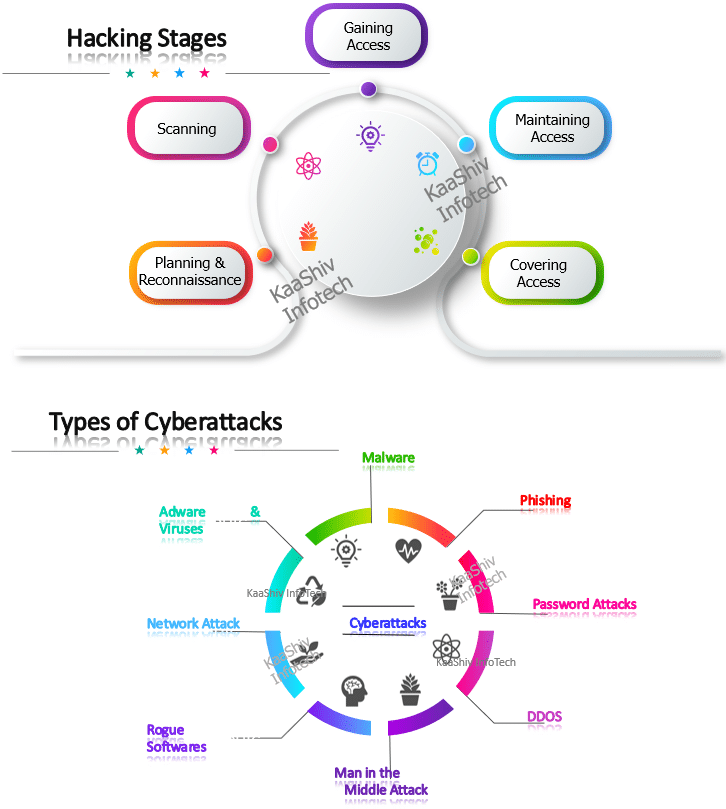
What are some of the common Cyberattacks ?
- Malware
- Phishing
- Password Attacks
- DDoS
- Man in the Middle
- Drive-By Downloads
- Malvertising
- Rogue Software
What is Phishing ?
- Phishing method includes sending of false emails, chats or website to the copy real system with aim of stealing data from the original website.

