iot projects for be –
IOT based Integral Atuthentication Security Option towards Unpredictable Patterns
Request for Project – [email protected] ; [email protected]
Contact Number – 7667668009 / 7667664842
Whatsapp Number – 7667668009 / 7667664842
For complete project lists – final year project for cse
For internship – internship in chennai
Abstract:
Enormous number of connected devices is growing exponentially day by day, forming the so-called Internet of Things (IoT), a large network of networks connecting smart devices such as sensors and actuators. Such devices are adopted in various domains such as
- public health,
- smart grids,
- smart transportation,
- waste management,
- smart homes,
- smart cities,
- agriculture,
- energy management, etc
Authentication is a obligatory factors of technological world concerned with security. Multi-factor authentication – also called two-factor authentication – secures access to networks and validates and protects user identities. In the existing methodology, an authentication by means of user security input in the form of text is utilized and converted to AdvancedCap. AdvancedCap “Completely Automated Public Turing“ is a type of challenge-response test used in computing to determine whether or not the user is human. The generated AdvancedCap is splited into two by the concept of visual cryptography in the server for authentication purposes and merged to verify the authenticity. In the proposed methodology, a Graphical Image Password has been designed that provides the users with an option to select the hotspots in the hierarchy of the images. The successive selection of the exact hot spots in the splited image will enable the user to move to the next successful images. These hotspots will be another way prominent way of authentication.
INTRODUCTION
- Synopsis:
Network Security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password.
- OBJECTIVE:
The thought of AdvancedCap to interpret the licensed human is incorporated that prevail the human illation with the server by crypto logic ideas. Image hotspot technique concomitant with the notion of AdvancedCap styles the system in increased approach with security live. A ordered image hotspots has been designed by suggests that of graphical illustration or clued points on the image taken. On the thriving traversal of the five ordered hotspot pictures ,the user get genuine to the server. The ordered traversal of hotspot image will been known by pattern matching situation so as to correlate the licensed user’s click points within the hotspot.
Scope:
To extend the multiple variety of hotspot level to avoid the vulnerability of the system. Conjointly the pattern matching technique wont to distinguishing the approved users supported our entered hotspot level.
SYSTEM STUDY
FEASIBILITY STUDY
The feasibility of the project is analyzed in this phase and business proposal is put forth with a very general plan for the project and some cost estimates. During system analysis the feasibility study of the proposed system is to be carried out. This is to ensure that the proposed system is not a burden to the company. For feasibility analysis, some understanding of the major requirements for the system is essential.
Three key considerations involved in the feasibility analysis are
- ECONOMICAL FEASIBILITY
- TECHNICAL FEASIBILITY
- SOCIAL FEASIBILITY
ECONOMICAL FEASIBILITY
This study is carried out to check the economic impact that the system will have on the organization. The amount of fund that the company can pour into the research and development of the system is limited. The expenditures must be justified. Thus the developed system as well within the budget and this was achieved because most of the technologies used are freely available. Only the customized products had to be purchased.
TECHNICAL FEASIBILITY
This study is carried out to check the technical feasibility, that is, the technical requirements of the system. Any system developed must not have a high demand on the available technical resources. This will lead to high demands on the available technical resources. This will lead to high demands being placed on the client. The developed system must have a modest requirement, as only minimal or null changes are required for implementing this system.
SOCIAL FEASIBILITY
The aspect of study is to check the level of acceptance of the system by the user. This includes the process of training the user to use the system efficiently. The user must not feel threatened by the system, instead must accept it as a necessity. The level of acceptance by the users solely depends on the methods that are employed to educate the user about the system and to make him familiar with it. His level of confidence must be raised so that he is also able to make some constructive criticism, which is welcomed, as he is the final user of the system.
- SYSTEM ANALYSIS on, be iot projects :
System Analysis is a combined process dissecting the system responsibilities that are based on the problem domain characteristics and user requirements.
- EXISTING SYSTEM:
- Security plays a major role in the authentication process in high severity applications. Passwords are the type of secret code used in the process of authentication.
- In the existing system, a AdvancedCap and picture based authentication is designed to authenticate into the system.
- The concept of visual cryptography has been integrated with the AdvancedCap for individual user and got splitted equally in order to store in the server.
- The Server provide authentication to the requestor thereby verifying the AdvancedCap by merging the splitted shares to ensures the authorized human interpretations.
- The authentication by means of picture also been the part of the existing methodology that has a feature of picture spot clicking password.
Disadvantages:
- The drawback of the existing system is that only a specific number of pictures can be utilized to set as a password and there is no successive cued clicks.
- The vulnerability of cracking the password is high that leads to insecurity.
2.2 be iot projects :PROPOSED SYSTEM:
- The projected system encompasses severe security outlook to design a secure authentication system.
- The concept of AdvancedCap to interpret the authorized human is incorporated that prevail the human inference with the server by cryptographic concepts.
- Image hotspot technique accompanying with the notion of AdvancedCap designs the system in enhanced way with security measure.
- Successive image hotspots have been designed by means of graphical representation or clued points on the image taken.
- On the thriving traversal of the 5 successive hotspot images, the user gets authenticated to the server.
- The successive traversal of hotspot image can been identified by pattern matching scenario in order to correlate the authorized user’s click points in the hotspot.
Advantages:
- The Advantages of the proposed system is to increase the multiple number of hotspot level to avoid the vulnerability of the system.
- Also the pattern matching technique used to identifying the authorized users based on our entered hotspot level.
SYSTEM REQUIREMENTS
3.2.1HARDWARE REQUIREMENTS for making – be iot projects :
- System : Pentium IV 2.4GHz.
- Hard Disk : 80 GB
- Monitor : 15VGA and High resolution monitor
- Mouse :
- Ram : 1 GB or Above
3.2.2 SOFTWARE REQUIREMENTS for making – be iot projects :
- Operating system : – Windows VISTA or Above.
- Front End : – Microsoft Visual Studio 2010
(.Net Framework 4.0)
- Coding Language : – C#(CSHARP)
- Backend : – Sql Server 2008 R2
SOFTWARE DESCRIPTION
4.1. Features Of .Net
Microsoft .NET is a set of Microsoft software technologies for rapidly building and integrating XML Web services, Microsoft Windows-based applications, and Web The Microsoft .NET Framework version 4.0 redistributable package (released 2010-04-12) installs the .NET Framework runtime and associated files that are required to run and develop applications to target the .NET Framework 4.
The Microsoft .NET Framework 4 provides the following new features and improvements:
- The .NET Framework 4 works side by side with the Framework version 3.5 SP1. Applications that are based on earlier versions of the Framework will continue to run on that version. Just a subset of functionality is shared by all versions of the Framework.
- Innovations in the Visual Basic and C# languages, for example statement lambdas, implicit line continuations, dynamic dispatch, and named/optional parameters.
- The ADO.NET Entity Framework, which simplifies how developers program against relational databases by raising the level of abstraction, has many new features. These includes persistence ignorance and POCO support, lazy loading, test-driven development support, functions in model, and new LINQ operators.
- Enhancements to ASP.NET : (used in implementing, be iot projects )
- New JavaScript UI Templates and databinding capabilities for AJAX.
- New ASP.NET chart control.
- Improvements in WPF:
- Added support in Windows Presentation Foundation (WPF) for Windows 7 multi-touch, ribbon controls, and taskbar extensibility features.
- Added support in WPF for Surface 2.0 SDK. o New line-of-business controls including charting control, smart edit, data grid, and others that improve the experience for developers who build data centric applications.
- Improvements in performance and scalability.
- Visual improvements in text clarity, layout pixel snapping, localization, and interoperability.
- Improvements to Windows Workflow (WF) that let developers to better host and interact with workflows. These include an improved activity programming model, an improved designer experience, a new flowchart modeling style, an expanded activity palette, workflow-rules integration, and new message correlation features. The .NET Framework also offers significant performance gains for WF-based workflows.
- Improvements to Windows Communication Foundation (WCF) such as support for WCF Workflow Services enabling workflow programs with messaging activities, correlation support, durable two-way communication and rich hosting capabilities. Additionally, .NET Framework 4 provides new WCF features such as service discovery, router service, simplified configuration and a number of improvements to queuing, REST support, diagnostics, and performance.
- Innovative new parallel programming features such as parallel loop support, Task Parallel Library (TPL), Parallel LINQ (PLINQ), and coordination data structures which let developers harness the power of multi-core processors.
4.2. THE .NET FRAMEWORK
The .NET Framework has two main parts:
- The Common Language Runtime (CLR).
- A hierarchical set of class libraries.
The CLR is described as the “execution engine” of .NET. It provides the environment within which programs run. The most important features are
- Conversion from a low-level assembler-style language, called Intermediate Language (IL), into code native to the platform being executed on.
- Memory management, notably including garbage collection.
- Checking and enforcing security restrictions on the running code.
- Loading and executing programs, with version control and other such features.
- The following features of the .NET framework are also worth description:
Managed Code in, be iot projects
The code that targets .NET, and which contains certain extra Information – “metadata” – to describe itself. Whilst both managed and unmanaged code can run in the runtime, only managed code contains the information that allows the CLR to guarantee, for instance, safe execution and interoperability.
Managed Data in, be iot projects
With Managed Code comes Managed Data. CLR provides memory allocation and Deal location facilities, and garbage collection. Some .NET languages use Managed Data by default, such as C#, Visual Basic.NET and JScript.NET, whereas others, namely C++, do not. Targeting CLR can, depending on the language you’re using, impose certain constraints on the features available. As with managed and unmanaged code, one can have both managed and unmanaged data in .NET applications – data that doesn’t get garbage collected but instead is looked after by unmanaged code.
Common Type System for – be iot projects
The CLR uses something called the Common Type System (CTS) to strictly enforce type-safety. This ensures that all classes are compatible with each other, by describing types in a common way. CTS define how types work within the runtime, which enables types in one language to interoperate with types in another language, including cross-language exception handling. As well as ensuring that types are only used in appropriate ways, the runtime also ensures that code doesn’t attempt to access memory that hasn’t been allocated to it.
In case of learning these technologies, you can opt for
- Internships like iot internship , iot internships or cloud computing internship
- trainings can be like iot taining in chennai , iot course or iot course in chennai or cloud computing training in chennai or cloud course in chennai
- Inplant training can be iot inplant training , cloud computing inplant training
Sample Code:
using System;
using System.Collections.Generic;
using System.Linq;
using System.Security.Cryptography;
using System.Text;
using System.Data;
using System.Data.SqlClient;
namespace ObjectAccess
{
public class ConnectDB
{
SqlConnection conn;
private string sqlpri;
public string sql
{
get
{
return sqlpri;
}
set
{
sqlpri = value;
}
}
public void OpenDB()
{
conn = new SqlConnection(@”Data Source=KAASHIV-PC\KINFOTECH;Integrated Security=true;Initial Catalog=OntheUser”);
//(ConfigurationManager.AppSettings[“DBConnection”].ToString());
conn.Open();
}
public int VerifyAdminCredentials(string usrName, string pwde)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand(“sp_VerifyAdminCredentials”, conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter(“@UserName”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@Password”, SqlDbType.VarChar));
cmd.Parameters[0].Value = usrName;
cmd.Parameters[1].Value = pwde;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public int VerifyDBACredentials(string usrName, string pwde,string dbaref)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand(“sp_VerifyDBACredentials”, conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter(“@UserName”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@Password”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@DBAReferenceNumber”, SqlDbType.VarChar));
cmd.Parameters[0].Value = usrName;
cmd.Parameters[1].Value = pwde;
cmd.Parameters[2].Value = dbaref;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public int VerifyCredentials(string usrName, string pwd,string UserProfile)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand(“sp_VerifyCredentials”, conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter(“@UserName”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@Password”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@UserProfile”, SqlDbType.VarChar));
cmd.Parameters[0].Value = usrName;
cmd.Parameters[1].Value = pwd;
cmd.Parameters[2].Value = UserProfile;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public int VerifyHighProfile(string passport, Guid RefNum)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand(“sp_VerifyHighProfile”, conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter(“@PassportNum”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@RefNum”, SqlDbType.UniqueIdentifier));
cmd.Parameters[0].Value = passport;
cmd.Parameters[1].Value = RefNum;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ((int)ds.Tables[0].Rows[0][0]);
}
public DataTable AddNewUser(string strFName, string strLName,
string UName, string Pwd, string DOB,
string Mobile, string SecurityQue, string SecurityAns,
string NativePlace,string PassportNumber,string MotherName,string BloodGroup,
string UserProfile)
{
OpenDB();
DataSet ds = new DataSet();
SqlDataAdapter adapter = new SqlDataAdapter();
SqlCommand cmd = new SqlCommand(“[sp_AddNewUser]”, conn);
cmd.CommandType = CommandType.StoredProcedure;
cmd.Parameters.Add(new SqlParameter(“@FirstName”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@LastName”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@UserName”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@Password”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@Mobile”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@DOB”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@PassportNumber”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@MotherName”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@BloodGroup”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@NativePlace”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@SecurityQuestion”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@SecurityAnswer”, SqlDbType.VarChar));
cmd.Parameters.Add(new SqlParameter(“@UserProfile”, SqlDbType.VarChar));
cmd.Parameters[0].Value = strFName;
cmd.Parameters[1].Value = strLName;
cmd.Parameters[2].Value = UName;
cmd.Parameters[3].Value = Pwd;
cmd.Parameters[4].Value = Mobile;
cmd.Parameters[5].Value = DOB;
cmd.Parameters[6].Value = PassportNumber;
cmd.Parameters[7].Value = MotherName;
cmd.Parameters[8].Value = BloodGroup;
cmd.Parameters[9].Value = NativePlace;
cmd.Parameters[10].Value = SecurityQue;
cmd.Parameters[11].Value = SecurityAns;
cmd.Parameters[12].Value = UserProfile;
adapter.SelectCommand = cmd;
adapter.Fill(ds);
conn.Close();
return ds.Tables[0];
}
public bool DoesUserExist(string username, string password)
{
OpenDB();
sql = “SELECT * FROM tblUserDetails WHERE UserName = ‘” + username +
“‘ AND Password = ‘” + password + “‘”;
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet dsResult = new DataSet();
string userExists = (cmd.ExecuteScalar() ?? “0”).ToString();
return userExists != “0”;
}
public string GetPublicKey(string Query)
{
OpenDB();
sql = “SELECT KeyGenerated FROM objectChangeScript where script = ‘” + Query+”‘”;
// mycolor = Color.Blue;
SqlCommand cmd = conn.CreateCommand();
cmd.CommandText = sql;
cmd.CommandType = CommandType.Text;
DataSet ds = new DataSet();
SqlDataAdapter da = new SqlDataAdapter(cmd);
da.Fill(ds);
return ds.Tables[0].Rows[0][0].ToString();
}
be iot projects – Sample Screenshots
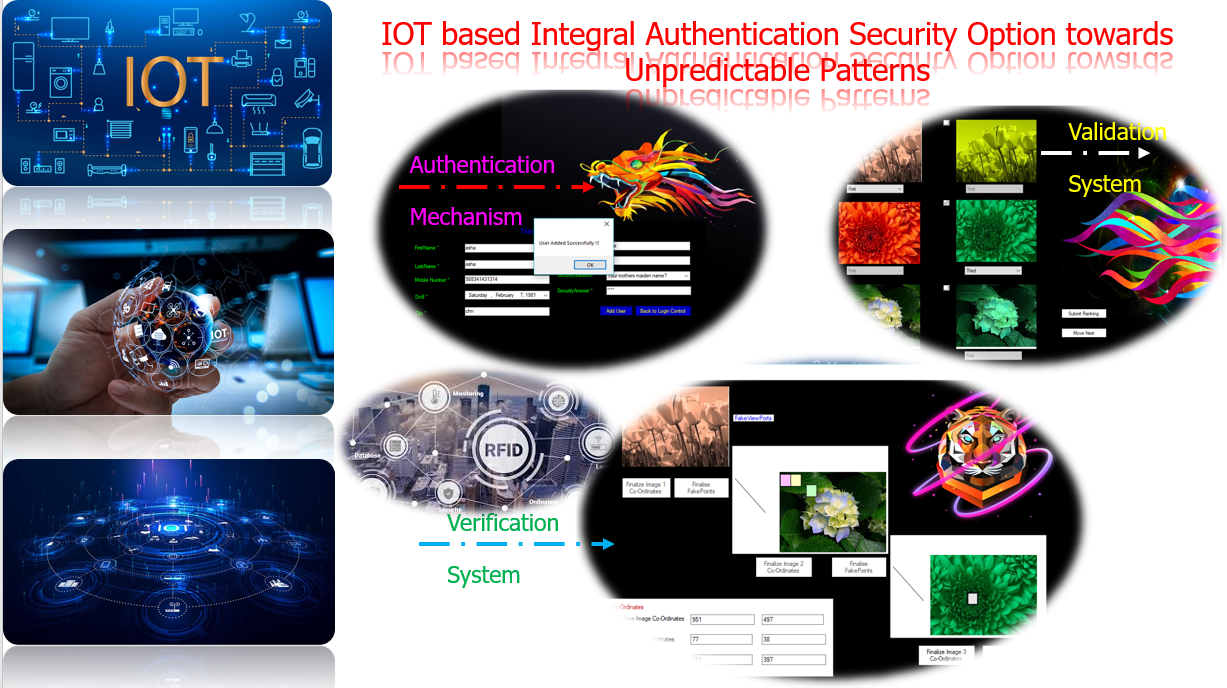
Contact Number – 7667668009 / 7667664842
Whatsapp Number – 7667668009 / 7667664842
For complete project lists – final year project for cse
For internship – internship in chennai


